It's almost January - the start of the Spring 2011 college semester. With my impending graduate school coursework comes the need for a laptop computer. I have been to several stores during the past several weeks, shopping price v.s. features. The college book store offers what seems like "sweetheart deals" on Dell laptops; you simply pick out the recommended machine based on the academic department for your course of study. While this seems like an easy option, and the package had lots of goodies thrown in, I was still put off by the $699 price tag. I ask myself "Do I really need all this or will a $349 Acer at Wal-Mart do as well?" Since I really don't yet know how much computer I really need, I decided to get advice from my instructor based on the actual demands of the curriculum before making a purchase.
One brand I have ELIMINATED is Dell - I will NOT have one of these unless some kind soul gives me a free one. Even then, I'd likely sell it on eBay and buy something else. Here's why:
A Descent Into (D)ell:
Recently, a neighbor asked me to look at his laptop and see if I could repair it. His girlfriend had dropped the machine and it had landed directly on the charger power plug, while it was still connected. This damaged the DC power connector on the laptop and the unit would no longer charge or even run off the AC adapter.
To make a very long story short
I replaced the connector, reassembled the laptop, and it still won't work from the AC adapter. Voltage checks with a DVM show all the connections to be good and that the AC adapter is supplying the proper voltage. The computer runs just fine from the battery; problem is right now there is no way of recharging the battery - and said battery is nearly depleted. On doing some online research, I found out Dell uses a special ID chip in all its AC power adapter/chargers - as well as its batteries. This ID chip "talks" to one located on the motherboard. If the computer does NOT recognize the power adapter/charger as a genuine Dell artifact, the machine will not charge the battery and may not even run, as in the case of my neighbor's unit. Same with the battery - if the computer does NOT recognize the battery as a genuine Dell artifact, it will not turn on.
During the fall, my neighbor's DC power connector got shorted out as a result of being smashed. Evidently this resulted in part of the ID system being damaged and disabled.
For more detailed technical information see the following links:
http://getsatisfaction.com/dell/topics/dell_laptop_wont_recognize_power_adapter_or_charge_battery
http://www.laptops-battery.co.uk/blog/dell-ac-power-adapter-type-cannot-be-determined-solution/
But wait, It gets even worse.
From my research, I've found that these chips fail regularly in both the AC charger units as well as the motherboards. MANY folks have been forced to buy replacement batteries and chargers because their ID chips and/or the three-pin charger power connectors got loose enough where the data line didn't make good connection any more. Dell's solution - buy new accessories and if the problem persists, replace the motherboard, a $330 dollar item as quoted to me by Dell tech support.
Several web sites have commented on the poor engineering and flimsy construction of these things but Dell continues to make them the same way.
While some other laptops also have ID chips in the batteries, I've found the Dell machines seem to garner by far the most complaints online.
A Possible Workaround
If you are in my neighbor's situation and don't want to or can't afford to shell out several hundreds of dollars to fix the problem, there is an external charger that will communicate with the battery's ID chip and thus be able to charge it out of the laptop.
http://www.laptop-junction.com/toast/content/standalone-laptop-battery-charger-dell-laptops
This is definitely a kluge, since you cannot simply plug the machine into AC power when the battery gets low and keep working. However, for those who cannot afford to replace the motherboard, or their entire machine, this is at least a way to retain partial use of it until a later time.
Conclusion
For those of us in the market for a new laptop, Let the buyer beware! If I can, I will select a machine that does NOT use multi-pin power connectors and ID chips for batteries and chargers. This, by itself, eliminates a potential source of unreliability in something I will have to depend on to get work done.
I also would like the option of running mine on off-grid power WITHOUT having to resort to a power inverter to feed the AC charger. Clearly a Dell would NOT be compatible with a home made battery supply or a solar panel without major internal hacking.
In view of the fragility of laptops and how difficult they generally are to repair, I highly recommend buying a 2-3 year extended warranty if the cost of such is no more than 1/3 of the everyday price of a comparable new machine. Even a cheap, "bottom of the barrel" laptop is a big enough investment that one would want to use it for at least 3 years - far longer than the 90 day to 1 year that most manufacturer's warranties last.
Sunday, December 26, 2010
Friday, November 19, 2010
Using gcc and g++ To Compile Programs In A LINUX Or Windows Environment
Many LINUX and most UNIX users are familiar with the gcc and g++ compilers. GCC stands for the "GNU Compiler Collection". GCC supports C, C++, JAVA, and a few others. GCC and g++ are available for free for most distributions of LINUX and UNIX. Many folks have used these utilities for both school projects as well as actual production development. The "GNU Compiler Collection" is ideal for developers, students, hobbyists, or anyone else wanting to work with or learn C/C++, JAVA, or Fortran on a shoestring and NOT shell out major funds for a commercial product. CygWin g++ and MinGW are designed for Windows machines; I've posted a link concerning this near the end of this post.
The gcc utility supports C, whereas g++ also supports C++.
GCC may be operated either from the command line or via a graphical IDE (Integrated Development Environment). Some folks also use it from within the vim or emacs text editors. I will cover the Code::Blocks IDE environment in a future post.
These are operated from the command line using commands such as the following:
gcc file.c
or
g++ file.c
Various command line switches such as -o, -g, ... tell it to save to a specific output file name, use the gdb debugger, etc.
The gcc and g++ compilers, by default, output to a file named a.out, unless you use the -o switch.
To compile a program and output to a filename of your choosing, such as "My_File", you would do the following:
gcc file.c -o My_File
To quickly test my compiler, I typed out the ever popular "Hello World" program in my text editor as shown below:
#include
main() {
printf("Hello from Karl's Lab!\n");
return 0;
}
and saved it as "Hello_Test.c" in my home directory. I wanted an output file called "Hello_1". I also wanted debugger information. Here's the command I used:
gcc Hello_Test.c -g -o Hello_1
The "-g" switch activated the gdb debugger; the -o Hello_1 part told it to name the output file "Hello_1"; "the "Hello_Test.c" part told it the name of the source file to be used.
When I typed "Hello_1" without the quotes at the command line, I received the following output:
Hello from Karl's Lab!
See a Compiler error:
In C, you must use the ";" symbol at the end of a statement. I wanted to see how gcc responds to an actual error, so I removed the ";" symbol from the "printf" line in the code snippet above, then saved and compiled the code as before. Here's the message it returned:
Hello_Test.c: In function ‘main’:
Hello_Test.c:7: error: expected ‘;’ before ‘return’
The first line of information shows the function - "main" - the error occurred in. The second line of output shows which line number the error occurred in and there is a ";" symbol missing in the code. While the actual typo was in line 4 of the code, the 'return' statement at line 7 is where the compiler errored out. With this output, you are at least given somewhere to start in trouble-shooting your code.
See the gdb debugger work:
Suppose your working directory is /home/mike/c_progs, and your executable is My_File. The command you would enter at the command line is:
gdb /home/mike/c_progs/My_File
You will get something like the following:
Copyright (C) 2008 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "i386-redhat-linux-gnu"...
(gdb)
At this (gdb) prompt, RUN "My_File" by typing "r" (without quotes).
(gdb) r
Starting program: /home/mike/c_progs/My_File
Hello from Mike!
Program exited normally.
This shows the program's output (Hello from Mike!), as well as that it executed without any errors or warnings.
When you are finished working, EXIT the gdb prompt by typing "q" without the quotes at the (gdb) prompt. This exits the debugger and returns you to the UNIX shell prompt.
Here are some good links on using gcc and g++ :
GCC's Homepage - Look here for the manuals to whatever version of gcc you have.
http://gcc.gnu.org/onlinedocs/
http://www.network-theory.co.uk/docs/gccintro/
Some good info for getting g++ for a Windows machine:
http://cocoon.cs.odu.edu/cocoon/~cs252/open/yourOwnCompiler/allPages.html
Here are some links to a good tutorial on the gdb debugger:
http://heather.cs.ucdavis.edu/~matloff/UnixAndC/CLanguage/Debug.html#tth_sEc3.2.1
and
http://www.cs.cmu.edu/~gilpin/tutorial/
The GCC Homepage:
http://gcc.gnu.org/
The gcc utility supports C, whereas g++ also supports C++.
GCC may be operated either from the command line or via a graphical IDE (Integrated Development Environment). Some folks also use it from within the vim or emacs text editors. I will cover the Code::Blocks IDE environment in a future post.
These are operated from the command line using commands such as the following:
gcc file.c
or
g++ file.c
Various command line switches such as -o, -g, ... tell it to save to a specific output file name, use the gdb debugger, etc.
The gcc and g++ compilers, by default, output to a file named a.out, unless you use the -o
To compile a program and output to a filename of your choosing, such as "My_File", you would do the following:
gcc file.c -o My_File
To quickly test my compiler, I typed out the ever popular "Hello World" program in my text editor as shown below:
#include
main() {
printf("Hello from Karl's Lab!\n");
return 0;
}
and saved it as "Hello_Test.c" in my home directory. I wanted an output file called "Hello_1". I also wanted debugger information. Here's the command I used:
gcc Hello_Test.c -g -o Hello_1
The "-g" switch activated the gdb debugger; the -o Hello_1 part told it to name the output file "Hello_1"; "the "Hello_Test.c" part told it the name of the source file to be used.
When I typed "Hello_1" without the quotes at the command line, I received the following output:
Hello from Karl's Lab!
See a Compiler error:
In C, you must use the ";" symbol at the end of a statement. I wanted to see how gcc responds to an actual error, so I removed the ";" symbol from the "printf" line in the code snippet above, then saved and compiled the code as before. Here's the message it returned:
Hello_Test.c: In function ‘main’:
Hello_Test.c:7: error: expected ‘;’ before ‘return’
The first line of information shows the function - "main" - the error occurred in. The second line of output shows which line number the error occurred in and there is a ";" symbol missing in the code. While the actual typo was in line 4 of the code, the 'return' statement at line 7 is where the compiler errored out. With this output, you are at least given somewhere to start in trouble-shooting your code.
See the gdb debugger work:
Suppose your working directory is /home/mike/c_progs, and your executable is My_File. The command you would enter at the command line is:
gdb /home/mike/c_progs/My_File
You will get something like the following:
Copyright (C) 2008 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "i386-redhat-linux-gnu"...
(gdb)
At this (gdb) prompt, RUN "My_File" by typing "r" (without quotes).
(gdb) r
Starting program: /home/mike/c_progs/My_File
Hello from Mike!
Program exited normally.
This shows the program's output (Hello from Mike!), as well as that it executed without any errors or warnings.
When you are finished working, EXIT the gdb prompt by typing "q" without the quotes at the (gdb) prompt. This exits the debugger and returns you to the UNIX shell prompt.
Here are some good links on using gcc and g++ :
GCC's Homepage - Look here for the manuals to whatever version of gcc you have.
http://gcc.gnu.org/onlinedocs/
http://www.network-theory.co.uk/docs/gccintro/
Some good info for getting g++ for a Windows machine:
http://cocoon.cs.odu.edu/cocoon/~cs252/open/yourOwnCompiler/allPages.html
Here are some links to a good tutorial on the gdb debugger:
http://heather.cs.ucdavis.edu/~matloff/UnixAndC/CLanguage/Debug.html#tth_sEc3.2.1
and
http://www.cs.cmu.edu/~gilpin/tutorial/
The GCC Homepage:
http://gcc.gnu.org/
Labels:
C,
C compiler,
C programming,
C++,
CygWin g++,
g++,
gcc,
LINUX,
MinGW,
Windows
Monday, November 15, 2010
Test of Ubuntu 10.10 "live" CD

Yesterday I tested Ubuntu 10.10 - Maverick Meerkat "live" CD release.
After downloading the iso file and burning it to CD, I booted my dual core 1.8 MHz machine to it. It took about 2.5 minutes to boot from the P.O.S.T. screen to the desktop. As I said in my last post, this is about typical of my experience with a "live" CD boot.
Ubuntu 10.10 auto-detected my HP printer and prompted me to install the HPLIP utility and drivers. Very cool!
Other observations:
1) This distribution has Open Office
2) Screen capture applet shows in the screen captures here - I suspect this is a bug
3) NO Gnu Image Manipulation Program (GIMP)
4) The gcc compiler does come with the "live" CD
5) The buttons to close, expand, or reduce active windows have been moved to the upper left-hand side of the windows. Why Canonical, the makers of Ubuntu, decided to do this, I don't know. I'm used to these functions being in the upper right hand corner of the window and prefer it that way.
6) Still the same GNOME desktop - the "Unity" desktop we've been hearing about lately is to occur in an upcoming "11" release.
7) As with Fedora 14, setting up my broadband access was a snap. A browser window may be seen in the following screenshot

I did not bother to try it on my 800 MHz Pentium III machine due to hardware issues.
You can get your own copy of Ubuntu 10.10 here:
www.ubuntu.com
Thursday, November 11, 2010
Test Of Fedora 14 'Live' CD Release
Last night, I decided to stay up late and try out the Fedora 14 live "Laughlin" CD release. I burned a CD from the iso file and booted my dual core machine to it. This machine is 1.8 MHz with 1 GB of RAM. Boot time was 1 minute 45 seconds. About typical in my experience for a CD ROM "live" run - booting from a CDROM and running the system entirely in RAM causes a bunch of latency you don't get in a "normal" installation. I figure a hard drive install will cut the boot time by about 2/3.

At two minutes, the desktop appeared as in the picture above. Fedora auto-detected my broadband connection, and Internet connectivity was easy and fast to set up. On checking the drop-down menu boxes, several things became apparent:
1) NO office productivity suite. Not surprising, as even as far back as Fedora Core 10, there was no office suite. I wonder if this has anything to do with the recent acquisition of Sun Microsystems and Open Office by Oracle. What WAS surprising to me was AbiWord wasn't even included. F.C.-10 at least included AbiWord.
2) NO GIMP - the GNU Image Manipulation Program. Not a huge problem, but past releases of Fedora had it and Ubuntu had it as of 10.04.
3) Firefox 3.6.10 - the most recent release - was included.
4) NO gcc, nmap, wireshark, or much else. What you are getting in the 'live' CD distro is a bare-bones system that will allow you to get online to download all the stuff you need for a decent system. As I found with Ubuntu 10, Ubuntu doesn't give you what they used to on the 'live' CD either. Would be interesting to try out a current Knoppix distro.
Subjective Impressions:
Once fully booted up, performance seemed average compared to my current Fedora hard drive installation. Online browsing with Firefox worked well with no apparent glitches. A browser window can be seen in the picture here.

Older, slower PIII system test:
Next, I tried the CD in my 800 MHz PIII 'coppermine' machine with 1 GB of RAM. This system normally runs acceptably well with an old Ubuntu 8.10 installation, but would NOT win any speed awards.
The first attempt at booting hung at two minutes into the game. I rebooted the machine and after four minutes got the desktop. While the mouse cursor moved about the desktop OK, the response when selecting menu items was extremely sluggish - to the point of being unusable.
This may NOT have been a fair test. I suspect it is developing some hardware issues; it does occasionally hang when booting Ubuntu 8.10. This was NOT a problem back in early 2009 when I first configured that system with Ubuntu 8.10, but it is increasingly so now. Another item I noticed is there were several error messages seen early during both boot attempts.
I don't have another working PIII system to test with, but I suspect FC-14 would work OK on this platform given more RAM (2 GB or more) and reliably functioning hardware.

At two minutes, the desktop appeared as in the picture above. Fedora auto-detected my broadband connection, and Internet connectivity was easy and fast to set up. On checking the drop-down menu boxes, several things became apparent:
1) NO office productivity suite. Not surprising, as even as far back as Fedora Core 10, there was no office suite. I wonder if this has anything to do with the recent acquisition of Sun Microsystems and Open Office by Oracle. What WAS surprising to me was AbiWord wasn't even included. F.C.-10 at least included AbiWord.
2) NO GIMP - the GNU Image Manipulation Program. Not a huge problem, but past releases of Fedora had it and Ubuntu had it as of 10.04.
3) Firefox 3.6.10 - the most recent release - was included.
4) NO gcc, nmap, wireshark, or much else. What you are getting in the 'live' CD distro is a bare-bones system that will allow you to get online to download all the stuff you need for a decent system. As I found with Ubuntu 10, Ubuntu doesn't give you what they used to on the 'live' CD either. Would be interesting to try out a current Knoppix distro.
Subjective Impressions:
Once fully booted up, performance seemed average compared to my current Fedora hard drive installation. Online browsing with Firefox worked well with no apparent glitches. A browser window can be seen in the picture here.

Older, slower PIII system test:
Next, I tried the CD in my 800 MHz PIII 'coppermine' machine with 1 GB of RAM. This system normally runs acceptably well with an old Ubuntu 8.10 installation, but would NOT win any speed awards.
The first attempt at booting hung at two minutes into the game. I rebooted the machine and after four minutes got the desktop. While the mouse cursor moved about the desktop OK, the response when selecting menu items was extremely sluggish - to the point of being unusable.
This may NOT have been a fair test. I suspect it is developing some hardware issues; it does occasionally hang when booting Ubuntu 8.10. This was NOT a problem back in early 2009 when I first configured that system with Ubuntu 8.10, but it is increasingly so now. Another item I noticed is there were several error messages seen early during both boot attempts.
I don't have another working PIII system to test with, but I suspect FC-14 would work OK on this platform given more RAM (2 GB or more) and reliably functioning hardware.
Wednesday, November 10, 2010
Fedora Core 14 LINUX
I recently downloaded the latest Fedora LINUX "live" CD release - Fedora Core 14. Hopefully within the next week or so I'll be able to actually test it. When that happens, I'll post the results and a couple screenshots here. Meanwhile I've been tied up with doing pre-winter maintenance on my truck, along with handling some other urgent personal matters.
Here is the link to the release notes for Fedora 14:
http://docs.fedoraproject.org/en-US/Fedora/14/html/Release_Notes/index.html
Get your very own copy of Fedora 14 here:
http://fedoraproject.org/en/get-fedora
If you want to try the desktop upgrade feature, you will need the "PreUpgrade" application. Go to http://fedoraproject.org/wiki/Upgradingfor more info.
In other news ...
I also plan to download and test out the new release of Ubuntu. Ubuntu has apparently switched from the traditional GNOME desktop to a new one. It will be interesting to see how that works.
Here is the link to the release notes for Fedora 14:
http://docs.fedoraproject.org/en-US/Fedora/14/html/Release_Notes/index.html
Get your very own copy of Fedora 14 here:
http://fedoraproject.org/en/get-fedora
If you want to try the desktop upgrade feature, you will need the "PreUpgrade" application. Go to http://fedoraproject.org/wiki/Upgradingfor more info.
In other news ...
I also plan to download and test out the new release of Ubuntu. Ubuntu has apparently switched from the traditional GNOME desktop to a new one. It will be interesting to see how that works.
It Snapped Clean Away - Replacing the Front Shocks On My Truck

Yesterday I decided to install new front shock absorbers on my rather elderly Ford truck. I've had the parts for a couple months, but decided I'd better get to it before Winter sets in.
Knowing the parts would be rusted, I sprayed them with WD-40 several times in the past week or two. This, in hopes some would penetrate and help the retaining nuts come loose when I removed them.
I started work on the passenger side. The nut on the top stud of the old shock was jammed on and wouldn't budge. Thinking I'd come back to it in a few minutes, I started work on the bottom stud. Within a minute or two,the bottom mounting nut came off all right - with the threaded end of the stud still stuck in it!! The rest of the stud was still attached to the truck and was holding the shock. [See above photo - bottom portion]I knew I was in trouble then - as the stud was a permanently attached part of the lower suspension arm. With the threaded portion broken off, there was no way to retain the bottom end of the new shock. After some proverbial head scratching, I went back in the house and got online to see how other folks handle this sort of problem. I quickly found out I was NOT alone - this problem is quite common. AND there is a reasonably inexpensive fix.
Fortunately, auto parts stores sell generic "Help" kits to replace broken shock mounting studs. Check places such as Autozone, NAPA, ... The new stud in the repair kit consists of a double-ended stud: the shock absorber mounts to the long, mostly smooth end; the short, slightly fatter threaded end goes into a hole in the frame or suspension member and mounts with a washer and nut. The old stud, of course, must be removed before the new one can be installed. Below I'll detail, in words and pictures, what I did.
Items needed:
New shock mounting stud repair kit - probably should get one for BOTH sides of the vehicle
hand-held "angle grinder" - preferably a 4.5" one. The wheel on a larger 5 or 6" one is too big and will be hitting stuff you don't want cut.
"Cut off" wheel and coarse grinding wheel for the grinder
an electric drill - preferably a 1/2" one
a set of drill bits - preferably titanium coated
A drill bit the right size for the new mounting stud in the repair kit you bought
Center punch and hammer
Here, in a nutshell, is what to do:
1) Use the angle grinder with "cut-off" wheel to remove the broken stud, cutting it off flush with the suspension or frame member it's attached to.
2) If necessary, use the angle grinder to cut through the top mounting stud on the shock absorber itself. That top stud is usually made of fairly mild steel, so one can cut partially through it and snap it off by pulling outward on the bottom end of the shock absorber. You may need to rock it back and forth a couple times, but it will break off with some effort. This is what I did, because the radius of the grinding wheel would have cut into stuff I didn't want damaged if I had gone clear through the stud. You will be working in tight quarters, so BE EXTREMELY CAREFUL to NOT cut the vehicle's coil spring or any other parts when using the grinder.

3) Use a center punch to mark dead center where the stud was.
4) Drill a hole where you made the punch mark. Start with a 1/8" drill and work up through your drill sizes to - in my case, a 1/2" hole - to accommodate the mounting stud. When drilling, coat the drill bit liberally with motor oil to help it cut.
5) On my vehicle, there was a 1/4" raised "shoulder" that was part of the old mounting stud - and was still on the lower suspension arm. I had to thin this down by 1/8" with the coarse wheel in the angle grinder so I could get the back mounting nut and washer fully threaded onto the new stud. Below is the picture of the hole drilled out and the shoulder ground down.
[Yes, I got the hole off center. Didn't start out that way, but I think the large drill bit "crept" out of the small pilot hole - I had to skip several drill sizes between my largest pilot drill and the final hole size. I also was drilling with a long bit at a really bad angle. At least there's enough shoulder metal remaining it shouldn't hurt anything. The rubber bushing on the new shock still has plenty of shoulder to bear against, so a washer wasn't necessary.]

6) Once the new stud is able to be nutted in place, you are ready to install the new shock. Below is the picture of the new shock installed.

Notes:
I got BOTH the shocks replaced within an hour and a half. The driver's side lower mounting stud did NOT break when I removed the nut, so all I had to do there is cut the top mounting stud on the shock and remove it as described in step 2 above.
Frankly, I expected the worst, given what immediately happened when I started the job. Thus I bought TWO repair kits so if the other one broke I'd have the parts right there.
My local auto supply store only had one lower shock mount repair kit in stock, but they were able to locate one in a neighboring area and get it held for me so I could drive over and get it.
I'm keeping my extra repair kit around in case I need it in the future.
I am eternally grateful to my neighbor for the use of his 4.5" angle grinder and 1/2" electric hand drill, as well as to several good folks on the Internet whose posts helped me deal with the problem at hand.
Sunday, October 31, 2010
Configuring Routers in SOHO Environments
Last week, I set up a LAN (local area network) at my house so I could share my Internet connection with other family members. Since my broadband modem only had provision for one device, I would need either a different broadband modem, or a router, to accommodate more than one work station. I checked with my ISP and was not terribly surprised when even THEY could not give me any information as to how best to set this up. They indicated they would allow up to four PCs to share the connection without incurring any additional charges. They were quite intent on "upgrading" me to their own wireless modem - for an additional $100 to purchase. I wasn't sure I even needed or wanted wireless, and in any event could buy newer equipment cheaper elsewhere. Instead I went out and purchased my own router, which can accommodate up to several computers or other network enabled devices.
In Brief - Why I have Written This Piece
A computer is NOT like a washing machine that you simply connect to utilities, use when you want it, and then forget it. But many folks unwittingly treat their PC that way - and that's how they get into trouble with lost data, 'catch' computer viruses, become victims of online ID theft, etc. Most folks I've met who have broadband modems or routers do not even have the internal firewall turned on, let alone properly set up. Many home and small business wireless networks are NOT secured properly; they're functioning as wireless public "hotspots" that anyone can connect to for whatever purpose - legal or otherwise. There are criminals who drive through neighborhoods with Wi-fi enabled laptop computers LOOKING for such unguarded networks through which to commit all manner of cyber crimes. I hope that anyone reading this who isn't already familiar with how to secure their home/small office networks can use this information to help improve their online security.
What a Router Does:
A router is used to connect two or more computer networks. When a router receives a data packet, it looks at the header information on that packet to see where it came from, and to what computer it is addressed to. The router checks to see if the packet is addressed to another computer on the same network where it originated, or if it needs to be transferred to another network. After determining where data packets it receives are coming from and addressed to, the router sends them where they need to go. In Small Office/Home Office (SOHO) environments, routers are often used so that several computers or even network enabled appliances such as TVs and game consoles can all share one internet connection. Some cable and DSL modems already have built-in routers and multiple Ethernet ports, while others (like mine) only have one connection.
Routers may either be "wired" or, "wireless" to provide 802.11 b,g or n Wi-fi access. Most "wireless" routers I've seen and dealt with also have provision for up to four RJ-45 Ethernet ports for connecting to wired computers.
Here are some GENERAL guidelines for choosing and setting up a router for SOHO use, based on my own research and on-the-job experience. This is NOT intended to be an exhaustive work; it is strictly intended to show some basic considerations for SOHO router setup. "Your mileage may vary" depending on your ISP, equipment, and particular needs:
1) Do you need Wi-fi (wireless) capability for laptops or other portable devices? If not, you might want to stay with a strictly WIRED Ethernet router. While many folks have adopted Wi-fi and love it, it is generally considered LESS safe or secure than wired. There is always the chance that criminals can hack into your router via your Wi-fi signal to access your Internet connection or networked PCs for nefarious purposes. If you MUST have Wi-fi, make sure your router/access point supports the newer and somewhat more secure WAP/WAP2 encryption protocols.
2) Firewall A built-in "hardware" firewall is mandatory. Whether buying a wired or wi-fi router, get one with a built-in firewall. Hardware firewalls placed between the Internet and your network perform a vital function by preventing certain types of cyber attacks from ever reaching your network in the first place. By contrast, "software" firewalls such as Zone Alarm, Windows Firewall, or the ones that come with the LINUX operating system, are installed on individual work stations and are a last line of resistance for them AFTER the network itself has been breached.
3) Configuration All routers, whether wired or wireless, that I have used have a 'configuration' web page that one logs into in order to set the thing up. Some have Windows software, a sort of "configuration wizard" on a CD, supplied with the device. I generally avoid using these, preferring to use the configuration web page instead. Once your PC is connected to the router, you can access the configuration web page by opening your web browser and pointing it to whatever local IP address your router's manual tells you. Generally it will be http://192.168.1.1, or sometimes http://192.168.1.100. You will be prompted for a username and password. The word "admin" or "administrator" is often the DEFAULT for BOTH the username and password. Again, check your manual for the exact login procedure.
Plug the router in, connect it to your PC - preferably with an Ethernet cable, and turn it on. Do NOT connect it to your DSL/broadband modem YET. Log in as described above, in keeping with the directions that came with your unit.
Once logged in, IMMEDIATELY do the following:
a) Change the default administrator username and passwords to something that others cannot easily guess. Especially for passwords, stay away from names of family members or pets, anniversary or birth dates, ... Also stay away from words that would appear in ANY language dictionary. A random string of letters and numbers is best; for something easier for you to remember you could also think of a sentence and pick the first or last letters of each word, then mix in some numbers. THAT is quite likely a good, strong password.
FAILURE to take this simple step may result in criminals easily getting in and reconfiguring your router, using your Internet connection for criminal activities - especially on wi-fi enabled routers, and/or attacking/hacking computers on your local network!!
b) AVOID taking the lazy way out by having Windows, or your web browser (in Windows or LINUX), remember the password! If your PC is ever compromised, that information may end up in the hands of bad people. Also, if you don't use the password you will forget it. Then it will be lost when your PC needs the inevitable reformat and re-install of its operating system. All you can do then is do a "hard reset" on the router to factory settings and reconfigure it from scratch. See your manual for how to do this.
c) Routers - often have a "network name" or, in the case of Wi-fi, a SSID (Service Set Identifier). Whichever default is there, whether it be "Belkin" or "Linksys", or whatever, should immediately be changed to something unrelated. Why make it any easier for the bad guys by TELLING THEM what brand of equipment you have? That just gives them an edge when probing your network for vulnerabilities. Also, avoid using your personal, family name, or business name for your network name or SSID as well - that identifies it as yours if someone wants to specifically mess with you. [This is NOT the 1950s any more, and growing numbers of people are having these sorts of problems nowadays.] For Wi-fi, the SSID should NEVER be broadcast unless you are setting up a public "hotspot". So make sure to select "Do not broadcast the SSID" in your wireless configuration menu. Anybody who is not authorized to connect to your network most surely does NOT need to know the SSID!
d) DHCP v.s. Static IP addresses - There are exceptions to this, but most home Internet connections use DHCP (Dynamic Host Configuration Protocol) for assigning you an IP address "on the fly". Most routers are by default set up to use DHCP to connect to the broadband modem. On your LAN (local area network), if you need to share files and/or printers, you will need LOCAL static IP addresses - usually in the 192.168.x.x range - for each of your PCs or networked printers. There are lots of good tutorials online for doing this. On the other hand, if you simply want a couple PCs to both have Internet access but NOT share files or printers, you could simply set them to use DHCP as well IF your router provides its own internal DHCP server for the LAN. Check your router's instruction manual/specs for more details.
e) Encrypted v.s. non-encrypted configuration access - If your router offers it, set the configuration page for "encrypted access"; it's MUCH safer! So, instead of pointing your browser to, say, http://192.168.1.1 to access the configuration page, you would now use https://192.168.1.1 as the IP for logging in. The https shows it's encrypted; the padlock symbol should display on your browser window when logged in this way.
f) Configuration login from outside - if you don't envision needing to log in to the router's configuration page from outside your local network, such as from a computer away from home, leave this DISABLED. This is yet another step in securing your network from unauthorized external access or changes.
g) Wi-fi access to configuration page - if your wi-fi router has provisions for this and one of your PCs is connected by wired Ethernet, DISABLE wireless access to the configuration page. This prevents someone from sitting in their car down the street and wirelessly hacking away at your router configuration page.
h) Wi-fi encryption - use the stronger WAP or "WAP2 Personal", rather than the weaker WEP encryption standard, on your wi-fi networked devices. "WAP/WAP2 Enterprise" is a whole different animal that requires an authentication server and is much more difficult to set up. Most SOHO networks don't currently use it.
i) MAC address filtering - every networked device, whether wired or wireless, has a unique hardware identifier called a MAC (Media Access Control) address. If your router offers MAC address filtering, use it. This further helps out by discriminating AGAINST any computer NOT listed in the router's MAC address lookup table. This also allows you to selectively shut off your kid's Internet access if he/she is misbehaving online. As an aside, you can find your computer's MAC address by opening a command prompt and typing "ipconfig" on a Windows box or "ifconfig" on a LINUX system. On my LINUX box, it is displayed by the ifconfig command in this format: "HWaddr 89:8A:2F:ED:5A:2G" . On any system, it will be a string of 6 pairs of hexadecimal numbers separated by colons - as in the above mentioned example. See your router's manual for how to set up MAC address filtering on your particular equipment.
j) On the firewall configuration, make sure the firewall is set to drop PING requests. Block any unused/unneeded ports if your router's firewall settings menu allows it. Port 80 needs to be open for basic Internet access, but often computers have other ports open by default that don't necessarily need to be. If you're strictly using web based email such as a "yahoo" account or Google's "gmail" through your browser, for example, as opposed to a POP3 server with MS Outlook, you can block the common ports used for POP3 email services. SMPT ports 25 and 110, for example. Many hardware firewalls allow blocking of access to certain sites or domains - good to know if you don't want your kids using Facebook, for example.
k) Wireless "peer to peer" or file sharing - DISABLE this if you don't really need it. Again, if you simply need a couple systems to access the Internet, but NOT share files or printers, this setting is safer. Obviously, if you DO need to share files and/or printers, then leave this ENABLED.
l) WAP Passphrase - make up a passphrase just as you did in step "a" above, though USE A DIFFERENT ONE. The WAP passphrase provides the basis for the encryption algorithm to work - and must be the same on BOTH the Wi-fi router and ANY client PC for them to work together. Again, use something that is not readily guessable or subject to a "dictionary attack".
Now, Test It Out
After you have done all this, go ahead and connect the router to the DSL/broadband modem. First test out any WIRED PC connections and make sure they can connect to the Internet. Correct any problems with the wired connections BEFORE dealing with the Wi-fi (if you have that). By doing things in this order, you have verified that your broadband/DSL connectivity and router are working BEFORE introducing any complications caused by Wi-fi issues.
Now, go back and configure any Wi-fi enabled PCs or laptops per any supplied instructions, using the same SSID settings, WAP encryption passphrases, ... as you did on the router. On many Windows PCs, you will need to reboot for the settings to take effect. Hopefully, if everything was configured properly, you will have Internet access on all your networked machines. If you ARE sharing files or printers, you will also need to configure those functions in the customary way for your equipment/operating system(s).
One caveat - bear in mind that many older wireless devices do NOT support WAP/WAP2 protocol. If you have an older PC or laptop with an older Wi-fi interface that cannot use WAP, you might want to consider buying a USB Wi-fi "dongle" that DOES support the newer protocol.
That's about all for now. While this is by far NOT a comprehensive tutorial on network security, it hopefully will help interested parties to avoid the most common mistakes.
In Brief - Why I have Written This Piece
A computer is NOT like a washing machine that you simply connect to utilities, use when you want it, and then forget it. But many folks unwittingly treat their PC that way - and that's how they get into trouble with lost data, 'catch' computer viruses, become victims of online ID theft, etc. Most folks I've met who have broadband modems or routers do not even have the internal firewall turned on, let alone properly set up. Many home and small business wireless networks are NOT secured properly; they're functioning as wireless public "hotspots" that anyone can connect to for whatever purpose - legal or otherwise. There are criminals who drive through neighborhoods with Wi-fi enabled laptop computers LOOKING for such unguarded networks through which to commit all manner of cyber crimes. I hope that anyone reading this who isn't already familiar with how to secure their home/small office networks can use this information to help improve their online security.
What a Router Does:
A router is used to connect two or more computer networks. When a router receives a data packet, it looks at the header information on that packet to see where it came from, and to what computer it is addressed to. The router checks to see if the packet is addressed to another computer on the same network where it originated, or if it needs to be transferred to another network. After determining where data packets it receives are coming from and addressed to, the router sends them where they need to go. In Small Office/Home Office (SOHO) environments, routers are often used so that several computers or even network enabled appliances such as TVs and game consoles can all share one internet connection. Some cable and DSL modems already have built-in routers and multiple Ethernet ports, while others (like mine) only have one connection.
Routers may either be "wired" or, "wireless" to provide 802.11 b,g or n Wi-fi access. Most "wireless" routers I've seen and dealt with also have provision for up to four RJ-45 Ethernet ports for connecting to wired computers.
Here are some GENERAL guidelines for choosing and setting up a router for SOHO use, based on my own research and on-the-job experience. This is NOT intended to be an exhaustive work; it is strictly intended to show some basic considerations for SOHO router setup. "Your mileage may vary" depending on your ISP, equipment, and particular needs:
1) Do you need Wi-fi (wireless) capability for laptops or other portable devices? If not, you might want to stay with a strictly WIRED Ethernet router. While many folks have adopted Wi-fi and love it, it is generally considered LESS safe or secure than wired. There is always the chance that criminals can hack into your router via your Wi-fi signal to access your Internet connection or networked PCs for nefarious purposes. If you MUST have Wi-fi, make sure your router/access point supports the newer and somewhat more secure WAP/WAP2 encryption protocols.
2) Firewall A built-in "hardware" firewall is mandatory. Whether buying a wired or wi-fi router, get one with a built-in firewall. Hardware firewalls placed between the Internet and your network perform a vital function by preventing certain types of cyber attacks from ever reaching your network in the first place. By contrast, "software" firewalls such as Zone Alarm, Windows Firewall, or the ones that come with the LINUX operating system, are installed on individual work stations and are a last line of resistance for them AFTER the network itself has been breached.
3) Configuration All routers, whether wired or wireless, that I have used have a 'configuration' web page that one logs into in order to set the thing up. Some have Windows software, a sort of "configuration wizard" on a CD, supplied with the device. I generally avoid using these, preferring to use the configuration web page instead. Once your PC is connected to the router, you can access the configuration web page by opening your web browser and pointing it to whatever local IP address your router's manual tells you. Generally it will be http://192.168.1.1, or sometimes http://192.168.1.100. You will be prompted for a username and password. The word "admin" or "administrator" is often the DEFAULT for BOTH the username and password. Again, check your manual for the exact login procedure.
Plug the router in, connect it to your PC - preferably with an Ethernet cable, and turn it on. Do NOT connect it to your DSL/broadband modem YET. Log in as described above, in keeping with the directions that came with your unit.
Once logged in, IMMEDIATELY do the following:
a) Change the default administrator username and passwords to something that others cannot easily guess. Especially for passwords, stay away from names of family members or pets, anniversary or birth dates, ... Also stay away from words that would appear in ANY language dictionary. A random string of letters and numbers is best; for something easier for you to remember you could also think of a sentence and pick the first or last letters of each word, then mix in some numbers. THAT is quite likely a good, strong password.
FAILURE to take this simple step may result in criminals easily getting in and reconfiguring your router, using your Internet connection for criminal activities - especially on wi-fi enabled routers, and/or attacking/hacking computers on your local network!!
b) AVOID taking the lazy way out by having Windows, or your web browser (in Windows or LINUX), remember the password! If your PC is ever compromised, that information may end up in the hands of bad people. Also, if you don't use the password you will forget it. Then it will be lost when your PC needs the inevitable reformat and re-install of its operating system. All you can do then is do a "hard reset" on the router to factory settings and reconfigure it from scratch. See your manual for how to do this.
c) Routers - often have a "network name" or, in the case of Wi-fi, a SSID (Service Set Identifier). Whichever default is there, whether it be "Belkin" or "Linksys", or whatever, should immediately be changed to something unrelated. Why make it any easier for the bad guys by TELLING THEM what brand of equipment you have? That just gives them an edge when probing your network for vulnerabilities. Also, avoid using your personal, family name, or business name for your network name or SSID as well - that identifies it as yours if someone wants to specifically mess with you. [This is NOT the 1950s any more, and growing numbers of people are having these sorts of problems nowadays.] For Wi-fi, the SSID should NEVER be broadcast unless you are setting up a public "hotspot". So make sure to select "Do not broadcast the SSID" in your wireless configuration menu. Anybody who is not authorized to connect to your network most surely does NOT need to know the SSID!
d) DHCP v.s. Static IP addresses - There are exceptions to this, but most home Internet connections use DHCP (Dynamic Host Configuration Protocol) for assigning you an IP address "on the fly". Most routers are by default set up to use DHCP to connect to the broadband modem. On your LAN (local area network), if you need to share files and/or printers, you will need LOCAL static IP addresses - usually in the 192.168.x.x range - for each of your PCs or networked printers. There are lots of good tutorials online for doing this. On the other hand, if you simply want a couple PCs to both have Internet access but NOT share files or printers, you could simply set them to use DHCP as well IF your router provides its own internal DHCP server for the LAN. Check your router's instruction manual/specs for more details.
e) Encrypted v.s. non-encrypted configuration access - If your router offers it, set the configuration page for "encrypted access"; it's MUCH safer! So, instead of pointing your browser to, say, http://192.168.1.1 to access the configuration page, you would now use https://192.168.1.1 as the IP for logging in. The https shows it's encrypted; the padlock symbol should display on your browser window when logged in this way.
f) Configuration login from outside - if you don't envision needing to log in to the router's configuration page from outside your local network, such as from a computer away from home, leave this DISABLED. This is yet another step in securing your network from unauthorized external access or changes.
g) Wi-fi access to configuration page - if your wi-fi router has provisions for this and one of your PCs is connected by wired Ethernet, DISABLE wireless access to the configuration page. This prevents someone from sitting in their car down the street and wirelessly hacking away at your router configuration page.
h) Wi-fi encryption - use the stronger WAP or "WAP2 Personal", rather than the weaker WEP encryption standard, on your wi-fi networked devices. "WAP/WAP2 Enterprise" is a whole different animal that requires an authentication server and is much more difficult to set up. Most SOHO networks don't currently use it.
i) MAC address filtering - every networked device, whether wired or wireless, has a unique hardware identifier called a MAC (Media Access Control) address. If your router offers MAC address filtering, use it. This further helps out by discriminating AGAINST any computer NOT listed in the router's MAC address lookup table. This also allows you to selectively shut off your kid's Internet access if he/she is misbehaving online. As an aside, you can find your computer's MAC address by opening a command prompt and typing "ipconfig" on a Windows box or "ifconfig" on a LINUX system. On my LINUX box, it is displayed by the ifconfig command in this format: "HWaddr 89:8A:2F:ED:5A:2G" . On any system, it will be a string of 6 pairs of hexadecimal numbers separated by colons - as in the above mentioned example. See your router's manual for how to set up MAC address filtering on your particular equipment.
j) On the firewall configuration, make sure the firewall is set to drop PING requests. Block any unused/unneeded ports if your router's firewall settings menu allows it. Port 80 needs to be open for basic Internet access, but often computers have other ports open by default that don't necessarily need to be. If you're strictly using web based email such as a "yahoo" account or Google's "gmail" through your browser, for example, as opposed to a POP3 server with MS Outlook, you can block the common ports used for POP3 email services. SMPT ports 25 and 110, for example. Many hardware firewalls allow blocking of access to certain sites or domains - good to know if you don't want your kids using Facebook, for example.
k) Wireless "peer to peer" or file sharing - DISABLE this if you don't really need it. Again, if you simply need a couple systems to access the Internet, but NOT share files or printers, this setting is safer. Obviously, if you DO need to share files and/or printers, then leave this ENABLED.
l) WAP Passphrase - make up a passphrase just as you did in step "a" above, though USE A DIFFERENT ONE. The WAP passphrase provides the basis for the encryption algorithm to work - and must be the same on BOTH the Wi-fi router and ANY client PC for them to work together. Again, use something that is not readily guessable or subject to a "dictionary attack".
Now, Test It Out
After you have done all this, go ahead and connect the router to the DSL/broadband modem. First test out any WIRED PC connections and make sure they can connect to the Internet. Correct any problems with the wired connections BEFORE dealing with the Wi-fi (if you have that). By doing things in this order, you have verified that your broadband/DSL connectivity and router are working BEFORE introducing any complications caused by Wi-fi issues.
Now, go back and configure any Wi-fi enabled PCs or laptops per any supplied instructions, using the same SSID settings, WAP encryption passphrases, ... as you did on the router. On many Windows PCs, you will need to reboot for the settings to take effect. Hopefully, if everything was configured properly, you will have Internet access on all your networked machines. If you ARE sharing files or printers, you will also need to configure those functions in the customary way for your equipment/operating system(s).
One caveat - bear in mind that many older wireless devices do NOT support WAP/WAP2 protocol. If you have an older PC or laptop with an older Wi-fi interface that cannot use WAP, you might want to consider buying a USB Wi-fi "dongle" that DOES support the newer protocol.
That's about all for now. While this is by far NOT a comprehensive tutorial on network security, it hopefully will help interested parties to avoid the most common mistakes.
Tuesday, October 19, 2010
What's Old Is New Again - Pre 1984 Telco Phones
Yes, it's been a while since I posted an entry here. Several work and family related issues have kept me quite busy.
Some of my interests may seem a bit anachronistic, especially when included on the same blog site with high tech solid state electronics and modern desktop PCs. Here is one example:
The Venerable "Plain ol' Telephone"
This past week, I bought a Western Electric model 2500 desk phone off eBay. It was built in 1980, according to the date code sticker on the bottom. This is the 'standard' touch tone desk phone common in America from the late 1960s through the 1980s. While I mainly got this because of nostalgia, the old telco provided phones also offer the following advantages:
1) More rugged construction - the telco supplied phones were generally quite robust and could take an amazing amount of abuse.
2) Often, the sound quality of the old phones is better than that of the newer models.
3) Fairly easy to service - Prior to the breakup of the Bell System in the early 1980s, customers generally rented their instruments from the phone company. Telephone company employees serviced these instruments in people's homes and businesses, thus these phones were made for fast, easy service and repair.
4) These are often quite a conversation piece, as there is a whole generation coming of age that has never used them!
When I got my phone in the mail today, I eagerly plugged it in and tried it out. The handset had that good, substantial heft I remembered from the past. The sound quality is good. But the touch tone pad did NOT work. Since the seller had a 100% rating and assured in the ad that it was "100% functional", I figured something might have happened during shipping. After all, this IS a 30-year old piece of equipment. After doing some research online, downloading some schematics, and verifying all the wiring was good using a DVM, I found out that many of the older touch tone pads are polarity sensitive. In other words, some phones will work if the line polarity is reversed, but many won't. My phone, with the 35-series dial, is one of the models that will NOT work if the phone line polarity is reversed. I simply reversed the incoming line connections and voila - it now works! I have posted several links I found useful in troubleshooting my old phone, as well as a couple sites that sell vintage repair parts and even show how you can safely use Grandma's "candlestick" style phone on today's telco systems!
Some Useful Resources For Those Interested In Plain Ol' Phones:
Parts and Repairs for Telephones
http://www.telephonetribute.com/parts_sources.htm
Phone Circuits and Stuff - even has some circuits for making your own 'hold' button, audio interfaces for amplifying/recording off the phone line, using old phones as intercoms, ... VERY useful stuff here!
http://www.epanorama.net/links/telephone.html#phonecircuits
Western Electric Touch Tone
http://www.porticus.org/bell/telephones-technical_dials-touchtone.html
Western Electric 500 Series Phones
http://www.paul-f.com/we500typ.htm#Model
Technical Documentation for Bell System Phones
http://www.paul-f.com/BSP.html
Believe it or not, you CAN still use ANY of those old rotary dial phones - even on those horrible voice menu systems that say "Press 1 for English", ... See the links below:
Old Phones, Parts, "Pulse-to-tone converters" - VERY cool site; lots of useful restoration parts and stuff! Probably will be shopping there soon.
http://www.oldphoneworks.com
Wiring a Touch Tone Pad to Any Antique Phone
http://atcaonline.com/ttpad.html
Some of my interests may seem a bit anachronistic, especially when included on the same blog site with high tech solid state electronics and modern desktop PCs. Here is one example:
The Venerable "Plain ol' Telephone"
This past week, I bought a Western Electric model 2500 desk phone off eBay. It was built in 1980, according to the date code sticker on the bottom. This is the 'standard' touch tone desk phone common in America from the late 1960s through the 1980s. While I mainly got this because of nostalgia, the old telco provided phones also offer the following advantages:
1) More rugged construction - the telco supplied phones were generally quite robust and could take an amazing amount of abuse.
2) Often, the sound quality of the old phones is better than that of the newer models.
3) Fairly easy to service - Prior to the breakup of the Bell System in the early 1980s, customers generally rented their instruments from the phone company. Telephone company employees serviced these instruments in people's homes and businesses, thus these phones were made for fast, easy service and repair.
4) These are often quite a conversation piece, as there is a whole generation coming of age that has never used them!
When I got my phone in the mail today, I eagerly plugged it in and tried it out. The handset had that good, substantial heft I remembered from the past. The sound quality is good. But the touch tone pad did NOT work. Since the seller had a 100% rating and assured in the ad that it was "100% functional", I figured something might have happened during shipping. After all, this IS a 30-year old piece of equipment. After doing some research online, downloading some schematics, and verifying all the wiring was good using a DVM, I found out that many of the older touch tone pads are polarity sensitive. In other words, some phones will work if the line polarity is reversed, but many won't. My phone, with the 35-series dial, is one of the models that will NOT work if the phone line polarity is reversed. I simply reversed the incoming line connections and voila - it now works! I have posted several links I found useful in troubleshooting my old phone, as well as a couple sites that sell vintage repair parts and even show how you can safely use Grandma's "candlestick" style phone on today's telco systems!
Some Useful Resources For Those Interested In Plain Ol' Phones:
Parts and Repairs for Telephones
http://www.telephonetribute.com/parts_sources.htm
Phone Circuits and Stuff - even has some circuits for making your own 'hold' button, audio interfaces for amplifying/recording off the phone line, using old phones as intercoms, ... VERY useful stuff here!
http://www.epanorama.net/links/telephone.html#phonecircuits
Western Electric Touch Tone
http://www.porticus.org/bell/telephones-technical_dials-touchtone.html
Western Electric 500 Series Phones
http://www.paul-f.com/we500typ.htm#Model
Technical Documentation for Bell System Phones
http://www.paul-f.com/BSP.html
Believe it or not, you CAN still use ANY of those old rotary dial phones - even on those horrible voice menu systems that say "Press 1 for English", ... See the links below:
Old Phones, Parts, "Pulse-to-tone converters" - VERY cool site; lots of useful restoration parts and stuff! Probably will be shopping there soon.
http://www.oldphoneworks.com
Wiring a Touch Tone Pad to Any Antique Phone
http://atcaonline.com/ttpad.html
Labels:
desk phone,
Model 2500,
Model 500,
telephone,
Western Electric
Tuesday, September 28, 2010
TS1 Test Fixture

Regular readers of this blog have seen a few of the automated test fixtures I have built.
Another fixture I built a few years ago monitors NEMA TS-1 output signals on up to 8 boards under test. TS-1 outputs are based on an open collector circuit configuration, producing a binary "low" or "high" condition. In simple terms these signals can be thought of as a "contact closure".
This fixture, as seen in the photos, contains a microcontroller and a couple "mux" boards for handling all the signals from two plug-in card cages. The TS1 fixture and card cages were mounted in a standard 19" rack cabinet. Each of the two card cages had a 33-conductor cable which plugs into the fixture - hence the pair of DB-37 female connectors seen in the top photo. These cables each handled 32 TS1 signals plus ground.
This device, as with the serial relay controller and the automated mouse movement emulator described in earlier blog posts, was controlled by a PC running LabVIEW software on Windows XP.

The box is an aluminum LMB enclosure; I used a dremmel tool to make the cut-outs for the DB-37 and DB-9 connectors, and a drill press for the round holes. The two large PCBs were made at an outside "board house", then populated by in-house assemblers. I mounted everything in the LMB enclosure and installed the chassis wiring. The smaller PCB - measuring about 2" x 2" - is the microcontroller board. The smallest PCB, connected to the microcontroller board via a ribbon cable, handles its RS-232 and power supply connections.
I built several of these fixtures for both engineering and manufacturing testing.
Monday, September 13, 2010
Of "Walled Gardens" and Computing Freedom
In an article entitled Intel's Walled Garden Plan to Put A/V Vendors Out of Business, Paul Otellini of Intel explained the reasoning behind its purchase of McAfee Anti Virus. Otellini described Intel's vision of "only allowing trusted and signed code" to run on the Intel x86 platform. The article went on to describe a scenario where you would get your software in a manner similar to the Apple "App Store" used on the iPhone.
Granted, the current security model purveyed by anti virus vendors is very labor intensive, inefficient, and all too often fails to catch a threat before it causes damage out in the world. Intel's model would offer a few advantages and probably eliminate some of the above-mentioned problems. If AV functionality was integral to the system's architecture, it would eliminate the problem of computer illiterate users not taking proper care of their PCs. The end user would not need to worry about installing anti virus software any more. All that said, this whole idea is NOT without significant shortcomings and impacts to system usability.
Users need to consider the following before they unconditionally embrace Intel's vision of a security utopia:
1) Just like on the iPhone, you would not be able to conveniently run software that wasn't approved by Intel/McAfee. Granted that some folks have found hacks to bypass the iPhone controls, but they do so at risk of other issues including violating their phone warranties.
2) Since software developers would have to deal with some "trusted" signing authority to get their code approved to run on Intel x86, this could well cause problems for open source users and developers - as much of this software is created on a low budget and often distributed for free.
3) What about folks writing their own code, scripts, etc.? No code you or I write on our computer would run until/unless it were signed by the "trusted" signing authority. This potentially includes batch files and UNIX/LINUX shell scripts.
4) An outgrowth of point 2 above, folks wanting to run LINUX, BSD, or other open source software could be in real trouble. At the very least, we could be forced into paying major dollars for our software to one or two large vendors who could afford the signing fees.
5) As one reader posted in the comments section, just because your software is "trusted" and signed does NOT mean it is without security holes or that it still couldn't cause trouble by running malicious code buried in a file.
6) Early in my career as a Windows user, I stopped using McAfee because of the severe impact it had on system resources. Several IT industry professionals I've talked to recommend other anti virus software as being more effective than McAfee at detecting viruses. I shudder at the thought of EVER using their products again on any computer I rely upon for critical work.
In Summary:
Clearly, there needs to be a new paradigm for secure computing. Cyber crime and terrorism are both a growing threat in today's world. That said, we need solutions that work for everyone. We need solutions that do not interfere with our freedom to use our machines for whatever LAWFUL purpose we want. We need solutions that allow us to continue running whatever OS or applications we FREELY choose. We do NOT need a "Nanny State" or "Nanny Company" solution to the problem.
Granted, the current security model purveyed by anti virus vendors is very labor intensive, inefficient, and all too often fails to catch a threat before it causes damage out in the world. Intel's model would offer a few advantages and probably eliminate some of the above-mentioned problems. If AV functionality was integral to the system's architecture, it would eliminate the problem of computer illiterate users not taking proper care of their PCs. The end user would not need to worry about installing anti virus software any more. All that said, this whole idea is NOT without significant shortcomings and impacts to system usability.
Users need to consider the following before they unconditionally embrace Intel's vision of a security utopia:
1) Just like on the iPhone, you would not be able to conveniently run software that wasn't approved by Intel/McAfee. Granted that some folks have found hacks to bypass the iPhone controls, but they do so at risk of other issues including violating their phone warranties.
2) Since software developers would have to deal with some "trusted" signing authority to get their code approved to run on Intel x86, this could well cause problems for open source users and developers - as much of this software is created on a low budget and often distributed for free.
3) What about folks writing their own code, scripts, etc.? No code you or I write on our computer would run until/unless it were signed by the "trusted" signing authority. This potentially includes batch files and UNIX/LINUX shell scripts.
4) An outgrowth of point 2 above, folks wanting to run LINUX, BSD, or other open source software could be in real trouble. At the very least, we could be forced into paying major dollars for our software to one or two large vendors who could afford the signing fees.
5) As one reader posted in the comments section, just because your software is "trusted" and signed does NOT mean it is without security holes or that it still couldn't cause trouble by running malicious code buried in a file.
6) Early in my career as a Windows user, I stopped using McAfee because of the severe impact it had on system resources. Several IT industry professionals I've talked to recommend other anti virus software as being more effective than McAfee at detecting viruses. I shudder at the thought of EVER using their products again on any computer I rely upon for critical work.
In Summary:
Clearly, there needs to be a new paradigm for secure computing. Cyber crime and terrorism are both a growing threat in today's world. That said, we need solutions that work for everyone. We need solutions that do not interfere with our freedom to use our machines for whatever LAWFUL purpose we want. We need solutions that allow us to continue running whatever OS or applications we FREELY choose. We do NOT need a "Nanny State" or "Nanny Company" solution to the problem.
Monday, August 23, 2010
HP Printer Support in LINUX
Last week I got around to fixing my printer issues on my Fedora box. As mentioned in a recent post, I had problems getting the HP printing software installed and working. As I also mentioned in a recent post, before trying to install applications or plugins, one should first apply ALL available and relevant system updates. Waiting until later to do this cost me much time and aggravation. There were updates to the CUPS printing software and other parts that were needed for the Laserjet printer or Open Office to install successfully. Once those updates were in place, I was able to quickly install the HP printing software and Open Office and get on with life.
Herein I will detail how I got printing enabled on my LINUX system, including hard-to-find but critical information on getting it to work on Fedora SE LINUX.
For those of us who own HP printers, there is a third party application called "HPLIP". This stands for "HP LINUX Imaging and Printing" and allows support for both printing and scanning. The following link will take you to the page where you may download HPLIP and also verify that your printer is supported:
http://hplipopensource.com/hplip-web/index.html
The download link will take you to another page where you will select your LINUX distribution and version, the printer type and model. Once you do this you will be given the correct version for your setup.
The following link tells you in excellent detail through words and screenshots how to run the HPLIP installer and what you will see on your screen at each step.
http://hplipopensource.com/hplip-web/install/install/index.html
BEFORE Installation:
BEFORE installing HPLIP, make sure your printer is DISCONNECTED from the computer!! The installer will prompt you when to connect the printer.
You need to be connected to the Internet during the entire installation, as your system will likely need to download other stuff to resolve dependencies. You will run the installer from the command line as detailed in the installation instructions.
Ubuntu:
Since the install instructions page shows a Ubuntu installation, things should proceed as in the pictures.
Installing on SE LINUX:
Fedora is quite similar to a Ubuntu installation EXCEPT you FIRST must disable the "SE" or "security enhanced" functionality in order to carry out the installation. [Your system will give you a message on the command line to this effect - this is NOT detailed in the step-by-step procedure shown in the above link]
Do the following:
1) Select the "SYSTEM" menu at the upper left-hand corner of your screen.
2) Select "Administration" ,
3) Choose "SE LINUX Management" from the drop-down menu that appears. You will be prompted for the root, or superuser password.
4) A window entitled "SE LINUX Administration" will appear within a few seconds.
Under "Status", you will see "system Default Enforcing mode", "Current Enforcing mode", and "system Default Policy type". Under "Current Enforcing Mode", select "Permissive".
5) Under "File" menu, select "quit" to log out of "SE LINUX Administration".
Once this is done, follow the instructions at the link above. The installer should do its thing.
Completing the Installation:
You should notice a blue "HP" logo in the upper right-hand portion of your screen.
You MAY be prompted to reboot or log out, then log back in.
If that is the case, you will need to run a "hp-setup" command from the command line to finish the installation. If you are running Fedora, you may need to disable SE functionality again as you did above. At this point, a dialog window will appear. This is the configuration window for setting up your printer. You will see a form to enter the printer name, description, and location [office, lab, ...]. Your system will search for a driver and should automatically download what it needs.
Select the "Print Test Page" button - if all has gone right you should be rewarded with a printout of the HPLIP test page.
IMPORTANT Fedora SE LINUX settings for Printing
After installing HPLIP, you should go back into the "SE LINUX Administration" menu and reset the "Current Enforcing Mode" to "Enforcing". Failure to do this will leave your system vulnerable to attacks!
In order to keep SE LINUX's "Current Enforcing Mode" set to "Enforcing" and STILL BE ABLE TO PRINT, do the following:
1) In the "SE LINUX Administration" menu, select "Process Domain"
2) Find "cupsd", cupsd_lpd", and "cups_pdf" - mark those "permissive" by clicking on each one and selecting the yellow "permissive" triangle symbol right above the list.
3) Click on the "file" menu, slect "close" so that the settings are saved and you are logged out of the "SE LINUX Management" menu.
4) Open a text file on your system and try printing it - it should print now even with "Current Enforcing Mode" set to "Enforcing".
Herein I will detail how I got printing enabled on my LINUX system, including hard-to-find but critical information on getting it to work on Fedora SE LINUX.
For those of us who own HP printers, there is a third party application called "HPLIP". This stands for "HP LINUX Imaging and Printing" and allows support for both printing and scanning. The following link will take you to the page where you may download HPLIP and also verify that your printer is supported:
http://hplipopensource.com/hplip-web/index.html
The download link will take you to another page where you will select your LINUX distribution and version, the printer type and model. Once you do this you will be given the correct version for your setup.
The following link tells you in excellent detail through words and screenshots how to run the HPLIP installer and what you will see on your screen at each step.
http://hplipopensource.com/hplip-web/install/install/index.html
BEFORE Installation:
BEFORE installing HPLIP, make sure your printer is DISCONNECTED from the computer!! The installer will prompt you when to connect the printer.
You need to be connected to the Internet during the entire installation, as your system will likely need to download other stuff to resolve dependencies. You will run the installer from the command line as detailed in the installation instructions.
Ubuntu:
Since the install instructions page shows a Ubuntu installation, things should proceed as in the pictures.
Installing on SE LINUX:
Fedora is quite similar to a Ubuntu installation EXCEPT you FIRST must disable the "SE" or "security enhanced" functionality in order to carry out the installation. [Your system will give you a message on the command line to this effect - this is NOT detailed in the step-by-step procedure shown in the above link]
Do the following:
1) Select the "SYSTEM" menu at the upper left-hand corner of your screen.
2) Select "Administration" ,
3) Choose "SE LINUX Management" from the drop-down menu that appears. You will be prompted for the root, or superuser password.
4) A window entitled "SE LINUX Administration" will appear within a few seconds.
Under "Status", you will see "system Default Enforcing mode", "Current Enforcing mode", and "system Default Policy type". Under "Current Enforcing Mode", select "Permissive".
5) Under "File" menu, select "quit" to log out of "SE LINUX Administration".
Once this is done, follow the instructions at the link above. The installer should do its thing.
Completing the Installation:
You should notice a blue "HP" logo in the upper right-hand portion of your screen.
You MAY be prompted to reboot or log out, then log back in.
If that is the case, you will need to run a "hp-setup" command from the command line to finish the installation. If you are running Fedora, you may need to disable SE functionality again as you did above. At this point, a dialog window will appear. This is the configuration window for setting up your printer. You will see a form to enter the printer name, description, and location [office, lab, ...]. Your system will search for a driver and should automatically download what it needs.
Select the "Print Test Page" button - if all has gone right you should be rewarded with a printout of the HPLIP test page.
IMPORTANT Fedora SE LINUX settings for Printing
After installing HPLIP, you should go back into the "SE LINUX Administration" menu and reset the "Current Enforcing Mode" to "Enforcing". Failure to do this will leave your system vulnerable to attacks!
In order to keep SE LINUX's "Current Enforcing Mode" set to "Enforcing" and STILL BE ABLE TO PRINT, do the following:
1) In the "SE LINUX Administration" menu, select "Process Domain"
2) Find "cupsd", cupsd_lpd", and "cups_pdf" - mark those "permissive" by clicking on each one and selecting the yellow "permissive" triangle symbol right above the list.
3) Click on the "file" menu, slect "close" so that the settings are saved and you are logged out of the "SE LINUX Management" menu.
4) Open a text file on your system and try printing it - it should print now even with "Current Enforcing Mode" set to "Enforcing".
Labels:
Fedora LINUX,
HP printer,
HPLIP,
Laserjet,
SE LINUX,
Ubuntu
Sunday, August 15, 2010
Mouse Movement Emulator - An Automated Test Fixture
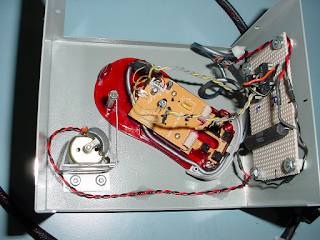
A while back, I posted a blog entry detailing a serial relay control fixture for automated testing. That device contained 48 relays that were individually controlled by RS-232 commands. A PC running LabVIEW software issued the control signals in the proper sequence, and collected and logged all data. One of the peripheral devices the serial relay fixture controlled was the mouse movement emulator described herein.
I designed this mouse movement emulator prototype - as seen in the picture - to generate signals for mouse movement, "left button clicks" and "right button clicks" without any human intervention required. The fixture consists of an optical mouse, two "dip" type relays, a vibrator motor to shake the mouse, and a resistor to reduce the current from a 12 volt supply to a safe level for the vibrator motor - which is rated for only 3 Vdc. The relays came from "in-house" parts stock; the vibrator motor, resistor, and aluminum chassis box were all bought from a local electronic supply house. A ceramic disc capacitor, visible in the picture, is connected across the motor's terminals. This capacitor, in conjunction with the current limiting resistor, forms a low-pass filter and helps supress electrical noise from the motor brushes.
The motor and relay control signals are transmitted through a 5-conductor cable which I made from separate pieces of hookup wire twisted together using an electric drill. The mouse signals are transmitted via the original gray colored shielded mouse cable. I threaded these two cables through a length of woven sheathing to keep them neat and tidy. A small section of the sheathed cable is visible in the lower left hand side of the picture. The cable is terminated in a male D-SUB connector which plugs into the serial relay control fixture.
Together with the serial relay control fixture and a PC running LabVIEW software, this device successfully exercises the mouse functions of the units under test (UUTs) WITHOUT a human being present to observe the test and/or operate the mouse.
Benifit for the project I was working on:
This unit made possible FULL automation of engineering design verification tests as well as manufacturing testing.
Verifying Checksums for LINUX Downloads - Part 2
On August 6, 2010, I posted an entry on how to verify checksums for downloaded LINUX CD .iso files. Herein is my own refinement on using the md5sum command.
The md5sum command:
For verifying the md5 chscksums [for Ubuntu 10.04, in this case], here is the basic command:
md5sum ubuntu-10.04-desktop-i386.iso
This generates an output like this to the command line:
d044a2a0c8103fc3e5b7e18b0f7de1c8 ubuntu-10.04-desktop-i386.iso
You then visually compare this to a similar string of letters and numbers taken from the md5 checksum file you downloaded along with the CD .iso file itself. Reading and comparing lines of gibberish like this can make you crosseyed. There IS a simple way to do this without spending a bunch of time or driving yourself crazy.
The way I do it:
As I pointed out in the August 6 post, I like to paste the output to a text file, along with the contents of the md5 file. To make this easier, I use the > symbol for UNIX redirect as follows:
md5sum ubuntu-10.04-desktop-i386.iso > sumcheck.txt
This creates a text file called "sumcheck.txt", then redirects the results from the md5sum command to it, rather than outputting to the command line as normal. You could actually use whatever name you want for the text file as long as it doesn't conflict with (and possibly over-write) something else on the system. I just happen to like the descriptive name "sumcheck". UNIX/LINUX allows you to forego using the .txt extension; I just do it to help when I'm looking at a directory listing from the command line.
Open "sumcheck.txt" in your "gedit" text editor wondow - you should see the output string generated by md5sum. Then, open the md5sum file you (hopefully) downloaded when you downloaded the cd .iso image. Copy the string seen there and paste it into your "sumcheck.txt" file on the line below your output string. Doing this results in the following:
d044a2a0c8103fc3e5b7e18b0f7de1c8 ubuntu-10.04-desktop-i386.iso
d044a2a0c8103fc3e5b7e18b0f7de1c8 *ubuntu-10.04-desktop-i386.iso
The top line was the output generated from the command I listed above.
The second line, the one with the asterisk, was the line copied and pasted from the downloaded md5 checksum file. See how at a glance you can quickly and easily compare the two strings?
After I'm done and am satisfied the files are not corrupted, I DELETE "sumcheck.txt" so I can use that filename again in the future.
The md5sum command:
For verifying the md5 chscksums [for Ubuntu 10.04, in this case], here is the basic command:
md5sum ubuntu-10.04-desktop-i386.iso
This generates an output like this to the command line:
d044a2a0c8103fc3e5b7e18b0f7de1c8 ubuntu-10.04-desktop-i386.iso
You then visually compare this to a similar string of letters and numbers taken from the md5 checksum file you downloaded along with the CD .iso file itself. Reading and comparing lines of gibberish like this can make you crosseyed. There IS a simple way to do this without spending a bunch of time or driving yourself crazy.
The way I do it:
As I pointed out in the August 6 post, I like to paste the output to a text file, along with the contents of the md5 file. To make this easier, I use the > symbol for UNIX redirect as follows:
md5sum ubuntu-10.04-desktop-i386.iso > sumcheck.txt
This creates a text file called "sumcheck.txt", then redirects the results from the md5sum command to it, rather than outputting to the command line as normal. You could actually use whatever name you want for the text file as long as it doesn't conflict with (and possibly over-write) something else on the system. I just happen to like the descriptive name "sumcheck". UNIX/LINUX allows you to forego using the .txt extension; I just do it to help when I'm looking at a directory listing from the command line.
Open "sumcheck.txt" in your "gedit" text editor wondow - you should see the output string generated by md5sum. Then, open the md5sum file you (hopefully) downloaded when you downloaded the cd .iso image. Copy the string seen there and paste it into your "sumcheck.txt" file on the line below your output string. Doing this results in the following:
d044a2a0c8103fc3e5b7e18b0f7de1c8 ubuntu-10.04-desktop-i386.iso
d044a2a0c8103fc3e5b7e18b0f7de1c8 *ubuntu-10.04-desktop-i386.iso
The top line was the output generated from the command I listed above.
The second line, the one with the asterisk, was the line copied and pasted from the downloaded md5 checksum file. See how at a glance you can quickly and easily compare the two strings?
After I'm done and am satisfied the files are not corrupted, I DELETE "sumcheck.txt" so I can use that filename again in the future.
Internet Radio for LINUX Users
As a longtime Internet radio fan, being able to continue listening was critical when I decided to switch to LINUX for my online activity. When I installed LINUX, I installed Adobe Flash, MP3 support, and other plugins for streaming media. With these I was able to access many, but not all sites I listened to/watched. Several radio stations I listen to require you to use a plugin called "Silverlight".
Silverlight is a microsoft browser plugin that many Internet radio stations use for their streaming media. It also supports graphics, multimedia, and interactive content. Windows users may use it with several browsers including Firefox; mac users can use it if they have Firefox.
Open Source to the rescue - again
For us LINUX users, there is "Moonlight". Moonlight is the open source option for LINUX/UNIX users. Check out these sites for the scoop on "Moonlight".
* Moonlight's Website - http://www.mono-project.com/Moonlight
* Moonlight Wiki - http://en.wikipedia.org/wiki/Moonlight_(runtime)
I got mine here from their LINUX Download site:
http://www.go-mono.com/moonlight/download.aspx
What To Do and What Happens:
Once on the site, click the download link to install the plugin. You will very likely be prompted by your system to enter the root (superuser) password. The download and install should proceed from there. As the Wiki page points out, the plugin does NOT include the actual codec, but the next time you navigate to a page that requires Silverlight, you will be prompted to download the codec FREE from Microsoft. Again, you will likely be prompted to enter the root password. Both downloads took less than 30 seconds at 300+ kbps speeds.
With Moonlight I was able to access those Internet radio stations which require the Silverlight plugin.
If you want more information on Silverlight, check out the following sites:
http://en.wikipedia.org/wiki/Microsoft_Silverlight
http://support.spacialaudio.com/wiki/Silverlight
Silverlight is a microsoft browser plugin that many Internet radio stations use for their streaming media. It also supports graphics, multimedia, and interactive content. Windows users may use it with several browsers including Firefox; mac users can use it if they have Firefox.
Open Source to the rescue - again
For us LINUX users, there is "Moonlight". Moonlight is the open source option for LINUX/UNIX users. Check out these sites for the scoop on "Moonlight".
* Moonlight's Website - http://www.mono-project.com/Moonlight
* Moonlight Wiki - http://en.wikipedia.org/wiki/Moonlight_(runtime)
I got mine here from their LINUX Download site:
http://www.go-mono.com/moonlight/download.aspx
What To Do and What Happens:
Once on the site, click the download link to install the plugin. You will very likely be prompted by your system to enter the root (superuser) password. The download and install should proceed from there. As the Wiki page points out, the plugin does NOT include the actual codec, but the next time you navigate to a page that requires Silverlight, you will be prompted to download the codec FREE from Microsoft. Again, you will likely be prompted to enter the root password. Both downloads took less than 30 seconds at 300+ kbps speeds.
With Moonlight I was able to access those Internet radio stations which require the Silverlight plugin.
If you want more information on Silverlight, check out the following sites:
http://en.wikipedia.org/wiki/Microsoft_Silverlight
http://support.spacialaudio.com/wiki/Silverlight
Labels:
Internet radio,
LINUX,
moonlight,
plugins,
silverlight
Tuesday, August 10, 2010
Home Garden Update - Alfalfa in Bloom

Regular readers of this blog may remember the earlier post regarding home gardening. For the past several years I have grown container gardens. This year I decided to experiment with some plants I had never grown before. These were yellow onions, cilantro, alfalfa, and romaine lettuce. I tried lavender last year but none of them germinated, so I tried again this year. I sprouted the lavender in some paper towels so I could see if they germinated. Once they sprouted, I moved them to potting soil.
My cilantro and lavender seeds germinated and produced some 1/4" shoots, but for whatever unknown reason these withered and died after about 3 weeks. I kept them watered and in what I thought was the right amount of sunlight. Same with the romaine lettuce - fortunately there is time to try that again before the cold season. I might try broccoli as well.
One of the items I had planted, mainly as an experiment, was a few alfalfa seeds. I did these in a small sweater box. They germinated and produced the plants seen in the picture above. I thought the blue flowers were cool and might be of interest to anyone who, like myself, had never grown alfalfa before. The plants appear "stretched". I think they probably need more sunlight then they get. This is problematic where I am located - due to the site geometry the plants are in shade most of the day. I may simply be unable to get decent results with certain crops due to the lack of direct sun.
Friday, August 6, 2010
You've just Installed Fedora Core LINUX 10,11,12, or 13: What to do now.
Before trying to install any new software or fix any problems, assuming you have internet connectivity, you need to apply any available system updates FIRST. Doing this can save you much time and headaches!
Some of the instructions you'll find posted online for doing this are out of date and actually apply for Fedora Core 9 or earlier. I think in some cases whoever 'wrote' the instructions simply copy and pasted text from the instructions for earlier releases.
Here's how to do it:
1) Run the software update viewer tool - look under the "System" menu, then under "Administration". Select "Update System" from the list. Running this will generate a list of software and files that can be updated.
2) At the very least, apply the security updates immediately.
3) Update any applications that you are having problems with. For example, if you are having problems getting your printer to work, and your printer IS supported, check the list for an update to CUPS or any of its libraries.
4) Beware of anything on the list you did NOT install. Mine listed some updates that don't even apply to me - for example, I do NOT have Apache HTTP server installed on my workstation machine, nonetheless there were a couple updates listed for Apache web server. I ignored those, as installing them will cause yum or RPM [the package manager] to "resolve" dependency issues by installing Apache - which I DID NOT WANT on this machine!
NOTE: Some versions, such as Fedora 10, had problems with the software updater which caused the graphical updater to "error out" - reporting "No network connection available". This happens even though you can surf the 'Net using your browser. This is a known problem covered on www.linuxquestions.org, and many folks apparently have NOT been able to fix it. If you are experiencing this, one workaround is to go down the list and install each update via the command line. Do the following:
su -
yum update [package name as listed]
NOTE - do NOT use the [ ] symbols when you type the command.
For example, say you want to install the library to access the contents of an ipod. Do the following:
su -
yum update libgpod-0.7.0-1.fc10
In this case, the "fc10" at the end indicates the package is for Fedora Core 10.
Note the package "gedit-1:2.24.3-3.fc10" has a number followed by a colon. When yum'ing for the package, you want to delete the colon and the number before it, as those will result in an error. I figured this out through experimentation - NOBODY I visited on the 'Net mentioned this.
So, say you want to update gedit to the following package - gedit-1:2.24.3-3.fc10.
Do the following:
su -
yum update gedit-2.24.3-3.fc10
As above, the "fc10" at the end indicates the package is for Fedora Core 10.
See how I dropped the 1 and the : after it?
As of this writing, Fedora is up to #13. If you are using 11, 12, or 13, your filenames will all end with .fc<11,12,or 13 - whatever your version is>
Fedora Complaints and Pet Peeves:
As I mentioned in a previous post, some of the repositories that are mentioned on other's web sites don't appear to work. I'm still in the process of hunting down repositories for some of my needed add-ons and plugins. As I find these I'll try to list those in future postings to this blog.
After a whole evening of not being able to find the gtstreamer plugins needed to update Totem player to handle MP3 files, I simply downloaded and installed Audacious - an application eerily similar to the old XMMS player. Works quite well and only took me a few minutes to get it.
The same issue with Totem gtstreamer plugins has so far prevented me from watching my DVD movies using Fedora.
I and quite a few other folks are having problems getting Open Office to work on Fedora. As soon as I find out anything definitive on this I'll post it.
My final complaint is with printing: My printer works fine with Ubuntu using the HPLIP printing software and drivers available online from sourceforge. Fedora, on the other hand, sees the printer but will not print to it. Am still working this issue as of this writing.
Some of the instructions you'll find posted online for doing this are out of date and actually apply for Fedora Core 9 or earlier. I think in some cases whoever 'wrote' the instructions simply copy and pasted text from the instructions for earlier releases.
Here's how to do it:
1) Run the software update viewer tool - look under the "System" menu, then under "Administration". Select "Update System" from the list. Running this will generate a list of software and files that can be updated.
2) At the very least, apply the security updates immediately.
3) Update any applications that you are having problems with. For example, if you are having problems getting your printer to work, and your printer IS supported, check the list for an update to CUPS or any of its libraries.
4) Beware of anything on the list you did NOT install. Mine listed some updates that don't even apply to me - for example, I do NOT have Apache HTTP server installed on my workstation machine, nonetheless there were a couple updates listed for Apache web server. I ignored those, as installing them will cause yum or RPM [the package manager] to "resolve" dependency issues by installing Apache - which I DID NOT WANT on this machine!
NOTE: Some versions, such as Fedora 10, had problems with the software updater which caused the graphical updater to "error out" - reporting "No network connection available". This happens even though you can surf the 'Net using your browser. This is a known problem covered on www.linuxquestions.org, and many folks apparently have NOT been able to fix it. If you are experiencing this, one workaround is to go down the list and install each update via the command line. Do the following:
su -
yum update [package name as listed]
NOTE - do NOT use the [ ] symbols when you type the command.
For example, say you want to install the library to access the contents of an ipod. Do the following:
su -
yum update libgpod-0.7.0-1.fc10
In this case, the "fc10" at the end indicates the package is for Fedora Core 10.
Note the package "gedit-1:2.24.3-3.fc10" has a number followed by a colon. When yum'ing for the package, you want to delete the colon and the number before it, as those will result in an error. I figured this out through experimentation - NOBODY I visited on the 'Net mentioned this.
So, say you want to update gedit to the following package - gedit-1:2.24.3-3.fc10.
Do the following:
su -
yum update gedit-2.24.3-3.fc10
As above, the "fc10" at the end indicates the package is for Fedora Core 10.
See how I dropped the 1 and the : after it?
As of this writing, Fedora is up to #13. If you are using 11, 12, or 13, your filenames will all end with .fc<11,12,or 13 - whatever your version is>
Fedora Complaints and Pet Peeves:
As I mentioned in a previous post, some of the repositories that are mentioned on other's web sites don't appear to work. I'm still in the process of hunting down repositories for some of my needed add-ons and plugins. As I find these I'll try to list those in future postings to this blog.
After a whole evening of not being able to find the gtstreamer plugins needed to update Totem player to handle MP3 files, I simply downloaded and installed Audacious - an application eerily similar to the old XMMS player. Works quite well and only took me a few minutes to get it.
The same issue with Totem gtstreamer plugins has so far prevented me from watching my DVD movies using Fedora.
I and quite a few other folks are having problems getting Open Office to work on Fedora. As soon as I find out anything definitive on this I'll post it.
My final complaint is with printing: My printer works fine with Ubuntu using the HPLIP printing software and drivers available online from sourceforge. Fedora, on the other hand, sees the printer but will not print to it. Am still working this issue as of this writing.
Downloading Fedora and Ubuntu LINUX: Verifying Checksums
For the last couple weeks I have had severe problems with my internet provider, and have not been able to post here. As you may have read in one of my earlier posts, this is not the first time. This week, I finally switched to a new ISP with broadband. Hopefully these folks will provide better and more reliable service. Thus far, it certainly promises to be faster than the other one.
Now that I have reasonably fast access, I decided to update my LINUX boxen to the latest releases. Since I run both Ubuntu and Fedora, I downloaded the current releases of both.
Checking File Integrity
When you download a LINUX distribution, or other software for that matter, it is good practice to use the checksum data, if supplied, to verify that your file is intact. This helps make sure the file wasn't corrupted during the download and that hopefully it hasn't been tampered with.
As a service to my fellow Ubuntu and Fedora users, I decided to post some instructions for doing this. Hopefully it will help someone.
For Ubuntu:
The following link offers helpful information:
https://help.ubuntu.com/community/HowToMD5SUM
In summary, here's what I did to check mine:
1) For the MD5SUM file, go to http://releases.ubuntu.com/, select the release you are interested in, then scroll down to the bottom of that page to find the MD5SUMS file. You can also find cd .iso files there to download.
2) Download the appropriate checksum file to the directory where you downloaded the cd .iso file to.
3) After downloading the md5 file [for Ubuntu 10.04 in this case], run the following from the command prompt:
md5sum ubuntu-10.04-desktop-i386.iso
You will (should) get an output such as this:
d044a2a0c8103fc3e5b7e18b0f7de1c8 ubuntu-10.04-desktop-i386.iso
Check this against the checksum file and make sure all the digits match.
Note that this also matches this line from the checksum file I downloaded:
d044a2a0c8103fc3e5b7e18b0f7de1c8 *ubuntu-10.04-desktop-i386.iso
This shows the .iso file matches the md5 checksum and so is probably not corrupted or been tampered with.
What I like to do is copy and paste these sets of numbers into a text file like this:
d044a2a0c8103fc3e5b7e18b0f7de1c8 *ubuntu-10.04-desktop-i386.iso
d044a2a0c8103fc3e5b7e18b0f7de1c8 ubuntu-10.04-desktop-i386.iso
This makes it easy to visually compare the two strings WITHOUT making yourself cross-eyed :)
If the strings match, you're good to go!! If not, then either your downloaded .iso is corrupted, or else you may be using the wrong checksum file.
For Fedora:
Fedora now does something different from the traditional md5sums command. They use something called sha256sum.
Here's how to do it:
First, you will need the appropriate checksum file for your .iso file.
For Fedora 13 checksums, go to
For 32 Bit, go to https://fedoraproject.org/static/checksums/Fedora-13-i386-CHECKSUM
For 64 bit, go to https://fedoraproject.org/static/checksums/Fedora-13-x86_64-CHECKSUM
For "Live" 32-bit desktop cd, go to https://fedoraproject.org/static/checksums/Fedora-13-i686-Live-CHECKSUM
For "Live" 64-bit desktop cd, go to https://fedoraproject.org/static/checksums/Fedora-13-x86_64-Live-CHECKSUM
Download and save the appropriate file to the same directory you downloaded your cd or DVD iso file to.
To check your downloaded iso, go to the command prompt and do the following:
1) Import the gpg keys by doing:
$ curl https://fedoraproject.org/static/fedora.gpg | gpg --import
2) Go to the directory you downloaded your iso file to.
3) Type the following command:
sha256sum -c Fedora-13-i686-Live-CHECKSUM if you are doing a "live" desktop cd, or
sha256sum -c Fedora-13-i386-CHECKSUM if you are doing the DVD or the several CD set.
You SHOULD get something like the following output if everything is OK:
Fedora-13-i686-Live.iso: OK
If you don't, then either your downloaded .iso is corrupted, or else you may be using the wrong checksum file.
Hope this helps someone.
Have fun!
Now that I have reasonably fast access, I decided to update my LINUX boxen to the latest releases. Since I run both Ubuntu and Fedora, I downloaded the current releases of both.
Checking File Integrity
When you download a LINUX distribution, or other software for that matter, it is good practice to use the checksum data, if supplied, to verify that your file is intact. This helps make sure the file wasn't corrupted during the download and that hopefully it hasn't been tampered with.
As a service to my fellow Ubuntu and Fedora users, I decided to post some instructions for doing this. Hopefully it will help someone.
For Ubuntu:
The following link offers helpful information:
https://help.ubuntu.com/community/HowToMD5SUM
In summary, here's what I did to check mine:
1) For the MD5SUM file, go to http://releases.ubuntu.com/, select the release you are interested in, then scroll down to the bottom of that page to find the MD5SUMS file. You can also find cd .iso files there to download.
2) Download the appropriate checksum file to the directory where you downloaded the cd .iso file to.
3) After downloading the md5 file [for Ubuntu 10.04 in this case], run the following from the command prompt:
md5sum ubuntu-10.04-desktop-i386.iso
You will (should) get an output such as this:
d044a2a0c8103fc3e5b7e18b0f7de1c8 ubuntu-10.04-desktop-i386.iso
Check this against the checksum file and make sure all the digits match.
Note that this also matches this line from the checksum file I downloaded:
d044a2a0c8103fc3e5b7e18b0f7de1c8 *ubuntu-10.04-desktop-i386.iso
This shows the .iso file matches the md5 checksum and so is probably not corrupted or been tampered with.
What I like to do is copy and paste these sets of numbers into a text file like this:
d044a2a0c8103fc3e5b7e18b0f7de1c8 *ubuntu-10.04-desktop-i386.iso
d044a2a0c8103fc3e5b7e18b0f7de1c8 ubuntu-10.04-desktop-i386.iso
This makes it easy to visually compare the two strings WITHOUT making yourself cross-eyed :)
If the strings match, you're good to go!! If not, then either your downloaded .iso is corrupted, or else you may be using the wrong checksum file.
For Fedora:
Fedora now does something different from the traditional md5sums command. They use something called sha256sum.
Here's how to do it:
First, you will need the appropriate checksum file for your .iso file.
For Fedora 13 checksums, go to
For 32 Bit, go to https://fedoraproject.org/static/checksums/Fedora-13-i386-CHECKSUM
For 64 bit, go to https://fedoraproject.org/static/checksums/Fedora-13-x86_64-CHECKSUM
For "Live" 32-bit desktop cd, go to https://fedoraproject.org/static/checksums/Fedora-13-i686-Live-CHECKSUM
For "Live" 64-bit desktop cd, go to https://fedoraproject.org/static/checksums/Fedora-13-x86_64-Live-CHECKSUM
Download and save the appropriate file to the same directory you downloaded your cd or DVD iso file to.
To check your downloaded iso, go to the command prompt and do the following:
1) Import the gpg keys by doing:
$ curl https://fedoraproject.org/static/fedora.gpg | gpg --import
2) Go to the directory you downloaded your iso file to.
3) Type the following command:
sha256sum -c Fedora-13-i686-Live-CHECKSUM if you are doing a "live" desktop cd, or
sha256sum -c Fedora-13-i386-CHECKSUM if you are doing the DVD or the several CD set.
You SHOULD get something like the following output if everything is OK:
Fedora-13-i686-Live.iso: OK
If you don't, then either your downloaded .iso is corrupted, or else you may be using the wrong checksum file.
Hope this helps someone.
Have fun!
Wednesday, July 21, 2010
A Few Thoughts On Obtaining Custom Machined Parts

If you do much building, creating, or inventing, you will have need of custom made parts that simply cannot be bought off the shelf. Many an inventor or engineer turns to a machine shop to make such parts. This solution is not without problems, however, and is usually out of reach of the average home hobbyist or tinkerer.
Despite the sorry state of the economy, machine shops charge a king's ransom these days even to do fairly simple jobs. This is, in part, due to the 'set-up' cost, any special tooling or jigs, ... required for doing a job. Much of the time and labor cost to fabricate something is taken up with preparation: laying it out, precision measuring, and readying the machine tools to do the work. Many machine shops concentrate on volume work and don't want to mess with "small" jobs, as they don't consider those profitable. While volume shops can amortize the set-up and tooling costs over a large number of widgets made, a prototype or short-run oriented shop must charge for that along with the materials and labor of making one or handful of parts. On a "one-off" job, the set-up often takes longer than making the part itself. Even in the unlikely event money is no object, try to find a local machine shop: it's nigh to impossible in many parts of the United States, given the off-shoring of manufacturing in the last 30 years. Sadly, very few young folks today are going into this trade. This is in part due to market forces, coupled with the general low esteem modern society has for "working with your hands" or "getting dirty".
Workarounds
Fortunately there are ways around the problem in many cases. Here are several ideas I've used:
1) If possible, change the design to use something that doesn't require expensive machining. Lots of things can be "re-purposed". One example: People have made wind-powered generators using a front brake rotor, wheel bearings, and spindle removed from a junked car.
2) If you must have something made 'from scratch', try to simplify your design to require as few machining steps as possible. Every step in the process of making a part requires more tooling and set-up, and thereby adds cost to the total project.
2) If you have access to a local community college or high school that offers a metal shop class for adults, you can take a course and gain access to the tools you need to do your project. As an aside, many people take auto shop classes in order to gain access to facilities and instructional advice for rebuilding classic cars.
3) Don't overlook resources at work. I was lucky enough for several years to work at a small engineering company that had its own machine shop. With the permission of my boss and the staff machinist, I was able to get some stuff done during lunch breaks and/or after hours.
4) Finally, you would be amazed at the stuff one can do in a pinch using simple hand tools, some skills, and much patience. For centuries prior to the advent of lathes, drill presses, and CNC machines, people made many things by hand that, to modern folk, would seem impossible. A couple examples include clocks that kept excellent time, and 10' long wooden blowguns with nice, smooth, straight bores.
I've mentioned Lindsay Publications in a previous blog post. These folks have reprinted many old, "outdated" manuals that detail long-forgotten skills that folks used to get things done prior to the modern era. They're online, or you can still order their books the old fashioned way by phone or 'snail'. Any inventor, engineer, hobbyist, tinkerer, or one interested in a more self-sufficient lifestyle would do well to regularly peruse Lindsay's book selection.
A "Simple" Project - Overcoming Some Challenges:
The photo above is of a 1.25" pipe plug I tapped for 1/4" NPT pipe. I pilot-drilled the hole to 1/8", then worked up in small drill size increments to a final hole size of 7/16". I tapped it using a Greenfield 1/4NPT TPR pipe tap bought from McMaster Carr. Note I tapped from BOTH ends, leaving a small unthreaded section in the center. I needed to be able to thread a pipe nipple into each side of the plug for a project I did a while back.
Sounds simple, right? Problem was I didn't have a tap handle that properly fit the tap nor did I have a good, bench-mounted machinist vice.
For a "tap handle" I used an adjustable "Crescent" type wrench to grip the square end of the tap. I turned the wrench with one hand, while using the palm of my other hand to press downward upon the "gripping" end of the wrench to drive the tap in straight. When I threaded the bottom side of the pipe plug, I was able to clamp it in an inverted position by its hex flange in my drill press vise, just as I had for drilling the hole. The threads in the top side were a bit more challenging.
As I mentioned previously, I didn't have a machinist bench vise available.
My drill press vise's jaws aren't deep enough to hold the plug's hex flange while I tapped that side. If I tried to clamp onto the threads I would ruin them and they would leak, assuming the plug would still even screw into a fitting afterward. So I bought a 1.25" pipe cap that I could clamp into the drill press vise. With the cap clamped securely, I simply screwed the plug into it and tapped the other side as before.
Not including the trip back to the hardware store to buy a pipe cap, this took about an hour to do all this. But it was MUCH cheaper and quicker than hiring a machine shop - ASSUMING they would even do a small job like this. I still did this myself in LESS time than I would take just to DRIVE to the nearest machine shop to pick up the work when it was done.
Granted, there are indeed some things, such as building a scroll type refrigeration compressor, that ARE impossible to do without some major machine shop tools. The original idea for that was conceived nearly 100 years ago, but it took the development of computerized machine tools to make the parts to the exacting tolerances needed for it to work. That said, many things can be and have been done under quite primitive - almost 'impossible' - circumstances.
Friday, July 2, 2010
Serial Relay Control Fixture

During my career as an electronic technician, I built many different test fixtures for both engineering and production testing. One thing nearly all automated test set-ups need is some PC-driven interface for controlling power and signals during testing. Enter the serial relay control fixture.
The serial relay fixture detailed here is used in an automated test tower to control power and signals to and from each of up to 8 assemblies, or units being tested (UUTs). This device consists of a 12 volt power supply, six RS-232 relay boards, connectors for each type of port, and quite a bit of interconnect wiring - all contained in an aluminum housing. As is shown in the above photo, there is both an exhaust fan as well as a filtered air intake port for ventilation. The cover is reversed in the photo showing the opened box - when assembled, the fan is normally positioned near the power supply to quickly remove the heat it generates. Each of the serial relay boards is uniquely addressable and contains 8 relays. Each of the relays is a DPDT unit which can be individually controlled with RS232 commands. Since there are six boards in the fixture, there are a total of 48 relays available for use.

Eight of these relays controlled power to each of the UUTs, most of the remaining ones switched signals between the UUTs and various pieces of gear. The RS-232 relay boards, a "commercial off-the-shelf" item, are PIC microcontroller based. These boards were designed such that up to 255 of them may be connected in parallel off the same RS-232 buss. Prior to being interconnected in this way, each one must be programmed individually by connecting it to a PC and assigning it a unique identifier number (address). Once this is done, each board can remember its address even if power is disconnected.
This fixture, as well as the complete refrigerator-size test tower it is a part of, is controlled via a Windows PC running LabVIEW software. The LabVIEW code performs two essential functions: it handles all the signals which control the sequence of the tests, and performs data acquisition via test gear equipped with GPIB or RS-232 ports. Each of the UUTs also communicates with another of the the PC's serial ports through a 16 port serial console switch - also controlled via the LabVIEW program.
While this serial relay control fixture was strictly used for control of an automated test tower, one could clearly use this same technology to accomplish other tasks - such as controlling industrial processes, or performing building automation functions.
Thursday, July 1, 2010
Getting JAVA to work in Firefox 3.66: The REAL Scoop
Recently, my Ubuntu LINUX box - a 2.4GHz P4 - suffered a catastrophic hardware failure. I will have to replace the motherboard, CPU, and memory. I have a dual-boot system with Windows VISTA and Fedora LINUX which I set up for experiments and for work on my graduate school classes. The Fedora box lacked some of the software I needed for email reading, listening to MP3s, ... that I did on the Ubuntu box. So under duress I scrambled to set it up to handle the slack.
After an evening-long battle, I have finally gotten most of the software installed that I need for important everyday business. Other than updating Firefox to the latest version (3.6.6 as of this writing), one of the most basic requirements is JAVA, since so many web sites use it extensively.
In order to get JAVA running in the Firefox browser in a LINUX environment, you need to add a symbolic link (symlink in IT speak) in your /usr/mozilla/plugins directory. In the past, the file one wanted to link to was libjavaplugin_oji.so. That all has changed, but most sites on the Internet have NOT caught up with the times! The file you NOW want to make your symlink to is libnpjp2.so.
Use the format of the instructions you read everywhere else, but you can generally use this default path to link the proper file:
/usr/java/jre1.6.0_20/lib/i386/libnpjp2.so
If your JAVA runtime engine is installed in another directory, or is a different version, modify the path accordingly.
Here's what to do:
Using the command line, navigate to your /usr/lib/mozilla/plugins directory (usual default path), su to root, and type the command seen below.
ln -s /usr/java/jre1.6.0_20/lib/i386/libnpjp2.so
As stated earlier, if your JAVA is installed in a location different than /usr/java, or if you are using a different release of JAVA, modify this command accordingly.
Then do a "ls" command and make sure the libnpjp2.so symlink appears.
Once this is done, you need to test your installation to make sure it works. Go to Sun's Java Test Page. Click on the link to verify your JAVA version. If all is working correctly you should get a message confirming what version of the JAVA runtime engine you are running.
MANY, many thanks to Albert Hayr for this information! You can reach his site here.
In a future post I'll cover which repositories actually DO have the plugins for MP3 playing. I'm finding that there's considerable wrong information on this as well.
See my update to this article here: ORACLE Java Issues.
After an evening-long battle, I have finally gotten most of the software installed that I need for important everyday business. Other than updating Firefox to the latest version (3.6.6 as of this writing), one of the most basic requirements is JAVA, since so many web sites use it extensively.
In order to get JAVA running in the Firefox browser in a LINUX environment, you need to add a symbolic link (symlink in IT speak) in your /usr/mozilla/plugins directory. In the past, the file one wanted to link to was libjavaplugin_oji.so. That all has changed, but most sites on the Internet have NOT caught up with the times! The file you NOW want to make your symlink to is libnpjp2.so.
Use the format of the instructions you read everywhere else, but you can generally use this default path to link the proper file:
/usr/java/jre1.6.0_20/lib/i386/libnpjp2.so
If your JAVA runtime engine is installed in another directory, or is a different version, modify the path accordingly.
Here's what to do:
Using the command line, navigate to your /usr/lib/mozilla/plugins directory (usual default path), su to root, and type the command seen below.
ln -s /usr/java/jre1.6.0_20/lib/i386/libnpjp2.so
As stated earlier, if your JAVA is installed in a location different than /usr/java, or if you are using a different release of JAVA, modify this command accordingly.
Then do a "ls" command and make sure the libnpjp2.so symlink appears.
Once this is done, you need to test your installation to make sure it works. Go to Sun's Java Test Page. Click on the link to verify your JAVA version. If all is working correctly you should get a message confirming what version of the JAVA runtime engine you are running.
MANY, many thanks to Albert Hayr for this information! You can reach his site here.
In a future post I'll cover which repositories actually DO have the plugins for MP3 playing. I'm finding that there's considerable wrong information on this as well.
See my update to this article here: ORACLE Java Issues.
Sunday, June 6, 2010
Homemade Hydraulic Press
Recently, the U-joints started failing on my truck's drive shaft. Many articles on this subject will tell you to us a large C-clamp or even a bench vise to press out the old bearing cups. Since I don't have a large enough bench vise to do this with, I opted for the C-clamp option. That didn't work out so well.
The C-clamp twisted and buckled when attempting to apply the necessary force to break the rusted parts loose. In the process of taking apart one U-joint I broke two C-clamps. I needed something considerably more stout, and the local auto parts stores didn't have any U-joint presses to rent. On thinking about the problem, I realized I could use a pair of thick metal bars with an allthread rod through either end with jam nuts to hold the bars in place. A "bottle" style hydraulic jack could sit on one bar while squeezing the workpiece against the other. A friend, who is a mechanical engineer, advised me on what thickness of metal to use and where I could buy it online.
The top and bottom "bars" are made of 9 lb/ft A-36 "C-channel" hot rolled steel and were ordered from "Speedy Metals". Their web site is www.speedymetals.com. These two pieces are 5" wide, 1.885" high, 0.325" thick, and each is 12" long. They were expensive - about $29 for the pair + another $16 for shipping. If my truck had been safe to drive the 20-30 miles EACH WAY I would have shopped locally at a scrap metal yard and possibly saved some dough. The "allthread" rods are each 3/4" in diameter and bought online from McMaster Carr at www.mcmaster.com. These, along with a suitable drill bit to make the holes for them, cost me almost $60.
A "posed" shot of the press appears below. This was taken after the work on the drive shaft had been completed. By then I was tired and did not take the time to "square up" the top bar as I would in actual use. Thus it looks crooked in the picture. At least you get the general idea of how it works:

Some Items of Note:
1) ALWAYS use eye protection - if something breaks under this much pressure shrapnel can fly everywhere!
2) This press worked quite well for its intended purpose, but as shown it is awkward to use. One almost needs a helper to steady it to keep the parts from flopping around while one sets up the work to be pressed.
3) I used regular, non-impact type wrench sockets. One was slightly smaller than the diameter of the bearing caps I was pressing; the other was slightly larger so as to support the drive shaft yoke while allowing the other bearing cap to pop out.
4) Lay the drive shaft on boxes, books, or whatever you have available so the yoke lines up with the top of the hydraulic jack and is thus square with it. That's why I had the black plastic "milk crate" in the photo located directly behind the press.
5) I soaked all parts with WD-40 spray the night before starting work on this project, as they were badly rusted.
6) When the rusted parts broke loose, they made quite a BANG along with a spark as the pent up energy was released. Definitely best to use this well away from any fumes that may be ignited by sparks.
7) All told, the metal, allthread rods, nuts, and the 7/8" drill bit used to drill the metal to accommodate the allthread, cost me a little over $100.
8) Drilling the holes - I thankfully own a drill press - bought at an estate sale - with a 1/2" chuck capacity. A 7/8" drill bit will have a 1/2" shank or larger. If you duplicate my project you will need either a drill press (ideally), or be strong enough to hold a 1/2" chuck electric hand drill steady when it goes through the bar and "grabs". In either case, use a few drops of motor oil on the drill bit and take it slowly. Failing all that you will need to find a friend with the appropriate equipment or perhaps take it to a machine shop.
9) When pumping the jack, take short, slow, gentle strokes. Do NOT pump the handle through its full vertical travel. This helps maintain better control of the pressure being exerted on the work.
10) A typical "bottle" style jack, available at most auto parts stores, can exert up to several tons of force. That said, use ONLY the amount of force you need - excessive force may bend or break expensive parts such as a drive shaft yoke.
Improvements I want to make:
1) Use either some more metal, or even 2X4 lumber, to make "feet" for the bottom bar of the press. I would also have the allthread rods clamped in some manner so that they are held vertical and don't flop around.
2) I've only had the metal in my possession for about 3 weeks, and already it is starting to rust due to the high humidity we've had. Cleaning and painting the metal channel bars with car engine paint and keeping the allthread oiled is clearly a good idea in view of this.
Granted, the press cost me a sizable fraction of what I could have paid to have the drive shaft professionally done - even with the current $80/hour shop rates in my area. However, I now have a tool that can be used on future projects.
The C-clamp twisted and buckled when attempting to apply the necessary force to break the rusted parts loose. In the process of taking apart one U-joint I broke two C-clamps. I needed something considerably more stout, and the local auto parts stores didn't have any U-joint presses to rent. On thinking about the problem, I realized I could use a pair of thick metal bars with an allthread rod through either end with jam nuts to hold the bars in place. A "bottle" style hydraulic jack could sit on one bar while squeezing the workpiece against the other. A friend, who is a mechanical engineer, advised me on what thickness of metal to use and where I could buy it online.
The top and bottom "bars" are made of 9 lb/ft A-36 "C-channel" hot rolled steel and were ordered from "Speedy Metals". Their web site is www.speedymetals.com. These two pieces are 5" wide, 1.885" high, 0.325" thick, and each is 12" long. They were expensive - about $29 for the pair + another $16 for shipping. If my truck had been safe to drive the 20-30 miles EACH WAY I would have shopped locally at a scrap metal yard and possibly saved some dough. The "allthread" rods are each 3/4" in diameter and bought online from McMaster Carr at www.mcmaster.com. These, along with a suitable drill bit to make the holes for them, cost me almost $60.
A "posed" shot of the press appears below. This was taken after the work on the drive shaft had been completed. By then I was tired and did not take the time to "square up" the top bar as I would in actual use. Thus it looks crooked in the picture. At least you get the general idea of how it works:

Some Items of Note:
1) ALWAYS use eye protection - if something breaks under this much pressure shrapnel can fly everywhere!
2) This press worked quite well for its intended purpose, but as shown it is awkward to use. One almost needs a helper to steady it to keep the parts from flopping around while one sets up the work to be pressed.
3) I used regular, non-impact type wrench sockets. One was slightly smaller than the diameter of the bearing caps I was pressing; the other was slightly larger so as to support the drive shaft yoke while allowing the other bearing cap to pop out.
4) Lay the drive shaft on boxes, books, or whatever you have available so the yoke lines up with the top of the hydraulic jack and is thus square with it. That's why I had the black plastic "milk crate" in the photo located directly behind the press.
5) I soaked all parts with WD-40 spray the night before starting work on this project, as they were badly rusted.
6) When the rusted parts broke loose, they made quite a BANG along with a spark as the pent up energy was released. Definitely best to use this well away from any fumes that may be ignited by sparks.
7) All told, the metal, allthread rods, nuts, and the 7/8" drill bit used to drill the metal to accommodate the allthread, cost me a little over $100.
8) Drilling the holes - I thankfully own a drill press - bought at an estate sale - with a 1/2" chuck capacity. A 7/8" drill bit will have a 1/2" shank or larger. If you duplicate my project you will need either a drill press (ideally), or be strong enough to hold a 1/2" chuck electric hand drill steady when it goes through the bar and "grabs". In either case, use a few drops of motor oil on the drill bit and take it slowly. Failing all that you will need to find a friend with the appropriate equipment or perhaps take it to a machine shop.
9) When pumping the jack, take short, slow, gentle strokes. Do NOT pump the handle through its full vertical travel. This helps maintain better control of the pressure being exerted on the work.
10) A typical "bottle" style jack, available at most auto parts stores, can exert up to several tons of force. That said, use ONLY the amount of force you need - excessive force may bend or break expensive parts such as a drive shaft yoke.
Improvements I want to make:
1) Use either some more metal, or even 2X4 lumber, to make "feet" for the bottom bar of the press. I would also have the allthread rods clamped in some manner so that they are held vertical and don't flop around.
2) I've only had the metal in my possession for about 3 weeks, and already it is starting to rust due to the high humidity we've had. Cleaning and painting the metal channel bars with car engine paint and keeping the allthread oiled is clearly a good idea in view of this.
Granted, the press cost me a sizable fraction of what I could have paid to have the drive shaft professionally done - even with the current $80/hour shop rates in my area. However, I now have a tool that can be used on future projects.
Thursday, May 6, 2010
A Great Source of Hard-To-Find Technical Information
Do you have any old machinery you want to restore? Have you ever wanted to know how metal is melted, poured, and then cast into useful objects? How about building a working steam engine? Wanna live "off the grid"? If you are doing your own home built windmill or generator set, you will definitely want their books on car alternator modification and power inverters. This, and much, much more is awaiting you at Lindsay's Technical Books. These people specialize in reprinting old technical manuals and how-to books. A couple caveats: Since they do mostly short runs, their inventory changes regularly. If you see something you like, you'd better get it immediately, as they may run out and NOT get any more copies. I have some fascinating books from them on steam engines, home-made machine shop equipment, metal casting, old radios, alternators and power inverters, ... Go to Lindsay Publications and check out their current offerings. And lest you wonder: NO, I do NOT have any financial interest in the company. I'm just one very satisfied customer.
Monday, April 26, 2010
Industrial Cleaning with Household Products
I have worked on lots of machines in my lifetime - cars and trucks, motorcycles, small engine powered equipment, HVAC systems, and most recently - machine shop tools. Part of the service usually involves cleanup of oil, grease, dirt, and/or other contamination.
In recent times, it has been increasingly difficult obtaining the solvents needed to get real work done. "Alkabrite(R)", which I'm told is basically an industrial lye solution, is no longer accepted in my area for use on kitchen refrigeration equipment. Many refrigeration houses I've talked to no longer carry it at all. A shame, as it is useful for de-greasing machinery of all types as well as for cleaning refrigeration and HVAC coils. If you work on cars you no doubt are familiar with Berryman's Chem-Dip(R) in the red, white, and blue bucket for carburetor cleaning. This, too, is becoming difficult to buy in many areas due to the restrictions on volatile organic compounds (VOCs).
Especially if you are unfortunate enough to live in the Southern California Air Quality Management District (SCAQMD), you may even find it difficult to purchase the so-called "eco-friendly" stuff. Some suppliers won't sell it to you unless you work for an auto repair shop, and when they do, they charge outrageous prices for the stuff.
Here, for what it's worth, are some workarounds I've found using readily available household products:
Simple Green(R)
Simple Green is relatively non-toxic and, as far as I know, non flammable. Unlike carburetor cleaner it will NOT asphyxiate or poison you with fumes, nor is it caustic to skin like Alkabrite(R) is. In aerosol form it is a lung and respiratory irritant, but used with care I have found it to be relatively safe compared to solvent based cleaners. Here's two unconventional uses I have found for this inexpensive and readily available product:
Air Conditioners Simple Green(R) works great for cleaning air conditioner and refrigeration coils. If the coils are dirty, performance will suffer and the evaporator (indoor) coil may freeze up due to restricted air flow. Filters should be changed at least once a season; the coils should be cleaned annually.
When I used Simple Green(R) commercially on motel window A/C units, I was amazed at how well it removed the several years' build-up of resinous tobacco grime and dirt from them. To do this, use plastic bags and duct tape to protect the motor and any other electrical parts. Fill a plastic spray bottle with a 50/50 mixture of Simple Green(R) and hot water. Spray this mixture on the coil and let it sit for 5-10 minutes. Using a garden hose and trigger-activated spray nozzle, carefully direct a spray of water through the coil from the INSIDE of the unit outward. Work slowly back and forth over the entire coil area. This will lift away much of the dirt and grime; the spray will also physically dislodge any impacted material from between the coil's aluminum fins. If there is still grime in the fins or on the surface, repeat application. Shine a flashlight through the coil from the back side - you should see light clearly through the fins - refracted only by water droplets. Depending on what was previously on them, the fins may be stained or oxidized, but there should be no oil, dirt, or grime left. When you are done, use a compressed air source to blow the excess moisture out of the fins and off of any other parts or assemblies. Do the "flashlight test" again - it should show a nice, clean coil free of any debris or obstruction.
CAUTIONS:
1) This seems obvious, but I'll say it anyway: You need to remove the unit from the window or wall it is installed in BEFORE trying this. I typically used a sidewalk, parking area, or driveway where I had a hard, dirt-free surface on which to work.
2) MAKE SURE all electrical parts are THOROUGHLY DRY before applying power - if you are unsure, or if you know water has leaked past your plastic bags and tape, use compressed air to blow any moisture from them and allow the unit to air-dry for a couple days.
3) I've used this technique on central HVAC systems, too, and it works quite well. You will have to be VERY careful of how much water you use so you don't overflow water out of the evaporator pan and onto your floor. Apply the water spray in short, quick blasts, allowing time for the water to be carried off by the drain. Depending on the design of your particular air handler, you may need a piece of sheet metal or thin plywood behind your coil to redirect spray and splatter back into the evaporator drain pan. Also, you will likely need to remove the squirrel cage blower from the unit to avoid getting water in the motor on these units.
4) Don't forget to do the OUTDOOR coils - as these also need cleaning.
5) Last but NOT LEAST: Be careful with the compressed air source - you can "mash" or collapse the fins if you use too much pressure. This will restrict the air flow when the unit is placed back in service. If you do mash some fins, use a "fin straightener" purchased from an HVAC supply house to GENTLY straighten them. This tool consists of a short handle with several interchangeable plastic "combs". These have teeth of differing thicknesses for different fin spacings. Use the one which most closely aligns with your coil's fins.
Carburetors
A couple years ago, I needed to clean the carburetor on my 20 year old portable generator. While I do have a bucket of Berryman's Chem Dip(R) for doing this sort of thing, I'm saving it for use only in an emergency or on the toughest jobs. Simple green(R) again came to the rescue here. Mix a 50/50 solution of Simple Green(R) and water sufficient to immerse the entire carburetor. Heat this in a metal container (NOT a pan you ever plan to cook food in!) on the stove to about 120 degrees F. This is somewhat hotter than bath water and warm enough to assure fast results, while still safe for most plastic parts. When I did this, all the garbage on both the outside and inside of the carb literally melted away in seconds! It made short work of the grayish colored gook left from gasoline that had sat in the float bowl for a couple years.
Disassemble your carb and soak the parts in the customary manner. I use a kitchen strainer for holding the small parts. I tie a wire to the large parts for dipping them in the hot solution. Periodically agitate the parts; I find that 20-30 minutes in the soak is usually plenty. When you are done, rinse your parts THOROUGHLY in running water. BE SURE to blow all the little tubes, ports, and passages clean with a compressed air source to remove dirt particles and water that could cause trouble later. Those cans of compressed air for blowing dirt out of PC cabinets work GREAT for this - and are a godsend for folks without access to an air compressor! The straw attachment on these cans allows you to direct the air blast right where you need it.
Neat Home-Made Goo for Removing Grease, Cosmoline(R), ...
Recently I helped a friend clean up some imported metal working equipment. This was coated with cosmoline(R) - a thick, toxic substance that often dries semi-hard and can be difficult to remove. Normally one would use some toxic cleaner bought from a hardware or auto parts store. Not wanting to use messy, toxic, and expensive chemicals - he came up with this substitute that's cheap, non-toxic, and actually works. With his kind permission, I have posted the recipe here:
Mix 2 - 3 parts lard (you buy it in a plastic tub at the grocery store) to 1 part vegetable oil. Use a fork and mash the ingredients together in a dish until you get a greasy paste that's roughly the thickness and appearance of phlegm. Adjust the ratio of lard to oil slightly as needed to get the desired consistency. Wearing rubber gloves, rub this mixture onto the surface that needs cleaning. Allow the mixture to sit. For something stubborn like cosmoline(R), you will want to allow an hour or more. Use a plastic spoon, plastic ice scraper, or the like to scrape off the worst of the mess. Use paper towels, followed up by a terry cloth shop rag, to rub the surface as clean as possible. If needed, re-apply the goop and let sit another 1/2 hour. Scrape off and wipe down as before. When you are done with this, you can either wash the surface with soap and water, then dry - or else simply wipe it clean with a fresh shop rag.
Bare metal surfaces should then be wiped with a light coat of machine oil to protect them from rust. Motor oil is okay in a pinch, too.
CAUTION: Remember that oily rags or paper towels can spontaneously combust under the right conditions - so dispose of these safely in a metal container.
In recent times, it has been increasingly difficult obtaining the solvents needed to get real work done. "Alkabrite(R)", which I'm told is basically an industrial lye solution, is no longer accepted in my area for use on kitchen refrigeration equipment. Many refrigeration houses I've talked to no longer carry it at all. A shame, as it is useful for de-greasing machinery of all types as well as for cleaning refrigeration and HVAC coils. If you work on cars you no doubt are familiar with Berryman's Chem-Dip(R) in the red, white, and blue bucket for carburetor cleaning. This, too, is becoming difficult to buy in many areas due to the restrictions on volatile organic compounds (VOCs).
Especially if you are unfortunate enough to live in the Southern California Air Quality Management District (SCAQMD), you may even find it difficult to purchase the so-called "eco-friendly" stuff. Some suppliers won't sell it to you unless you work for an auto repair shop, and when they do, they charge outrageous prices for the stuff.
Here, for what it's worth, are some workarounds I've found using readily available household products:
Simple Green(R)
Simple Green is relatively non-toxic and, as far as I know, non flammable. Unlike carburetor cleaner it will NOT asphyxiate or poison you with fumes, nor is it caustic to skin like Alkabrite(R) is. In aerosol form it is a lung and respiratory irritant, but used with care I have found it to be relatively safe compared to solvent based cleaners. Here's two unconventional uses I have found for this inexpensive and readily available product:
Air Conditioners Simple Green(R) works great for cleaning air conditioner and refrigeration coils. If the coils are dirty, performance will suffer and the evaporator (indoor) coil may freeze up due to restricted air flow. Filters should be changed at least once a season; the coils should be cleaned annually.
When I used Simple Green(R) commercially on motel window A/C units, I was amazed at how well it removed the several years' build-up of resinous tobacco grime and dirt from them. To do this, use plastic bags and duct tape to protect the motor and any other electrical parts. Fill a plastic spray bottle with a 50/50 mixture of Simple Green(R) and hot water. Spray this mixture on the coil and let it sit for 5-10 minutes. Using a garden hose and trigger-activated spray nozzle, carefully direct a spray of water through the coil from the INSIDE of the unit outward. Work slowly back and forth over the entire coil area. This will lift away much of the dirt and grime; the spray will also physically dislodge any impacted material from between the coil's aluminum fins. If there is still grime in the fins or on the surface, repeat application. Shine a flashlight through the coil from the back side - you should see light clearly through the fins - refracted only by water droplets. Depending on what was previously on them, the fins may be stained or oxidized, but there should be no oil, dirt, or grime left. When you are done, use a compressed air source to blow the excess moisture out of the fins and off of any other parts or assemblies. Do the "flashlight test" again - it should show a nice, clean coil free of any debris or obstruction.
CAUTIONS:
1) This seems obvious, but I'll say it anyway: You need to remove the unit from the window or wall it is installed in BEFORE trying this. I typically used a sidewalk, parking area, or driveway where I had a hard, dirt-free surface on which to work.
2) MAKE SURE all electrical parts are THOROUGHLY DRY before applying power - if you are unsure, or if you know water has leaked past your plastic bags and tape, use compressed air to blow any moisture from them and allow the unit to air-dry for a couple days.
3) I've used this technique on central HVAC systems, too, and it works quite well. You will have to be VERY careful of how much water you use so you don't overflow water out of the evaporator pan and onto your floor. Apply the water spray in short, quick blasts, allowing time for the water to be carried off by the drain. Depending on the design of your particular air handler, you may need a piece of sheet metal or thin plywood behind your coil to redirect spray and splatter back into the evaporator drain pan. Also, you will likely need to remove the squirrel cage blower from the unit to avoid getting water in the motor on these units.
4) Don't forget to do the OUTDOOR coils - as these also need cleaning.
5) Last but NOT LEAST: Be careful with the compressed air source - you can "mash" or collapse the fins if you use too much pressure. This will restrict the air flow when the unit is placed back in service. If you do mash some fins, use a "fin straightener" purchased from an HVAC supply house to GENTLY straighten them. This tool consists of a short handle with several interchangeable plastic "combs". These have teeth of differing thicknesses for different fin spacings. Use the one which most closely aligns with your coil's fins.
Carburetors
A couple years ago, I needed to clean the carburetor on my 20 year old portable generator. While I do have a bucket of Berryman's Chem Dip(R) for doing this sort of thing, I'm saving it for use only in an emergency or on the toughest jobs. Simple green(R) again came to the rescue here. Mix a 50/50 solution of Simple Green(R) and water sufficient to immerse the entire carburetor. Heat this in a metal container (NOT a pan you ever plan to cook food in!) on the stove to about 120 degrees F. This is somewhat hotter than bath water and warm enough to assure fast results, while still safe for most plastic parts. When I did this, all the garbage on both the outside and inside of the carb literally melted away in seconds! It made short work of the grayish colored gook left from gasoline that had sat in the float bowl for a couple years.
Disassemble your carb and soak the parts in the customary manner. I use a kitchen strainer for holding the small parts. I tie a wire to the large parts for dipping them in the hot solution. Periodically agitate the parts; I find that 20-30 minutes in the soak is usually plenty. When you are done, rinse your parts THOROUGHLY in running water. BE SURE to blow all the little tubes, ports, and passages clean with a compressed air source to remove dirt particles and water that could cause trouble later. Those cans of compressed air for blowing dirt out of PC cabinets work GREAT for this - and are a godsend for folks without access to an air compressor! The straw attachment on these cans allows you to direct the air blast right where you need it.
Neat Home-Made Goo for Removing Grease, Cosmoline(R), ...
Recently I helped a friend clean up some imported metal working equipment. This was coated with cosmoline(R) - a thick, toxic substance that often dries semi-hard and can be difficult to remove. Normally one would use some toxic cleaner bought from a hardware or auto parts store. Not wanting to use messy, toxic, and expensive chemicals - he came up with this substitute that's cheap, non-toxic, and actually works. With his kind permission, I have posted the recipe here:
Mix 2 - 3 parts lard (you buy it in a plastic tub at the grocery store) to 1 part vegetable oil. Use a fork and mash the ingredients together in a dish until you get a greasy paste that's roughly the thickness and appearance of phlegm. Adjust the ratio of lard to oil slightly as needed to get the desired consistency. Wearing rubber gloves, rub this mixture onto the surface that needs cleaning. Allow the mixture to sit. For something stubborn like cosmoline(R), you will want to allow an hour or more. Use a plastic spoon, plastic ice scraper, or the like to scrape off the worst of the mess. Use paper towels, followed up by a terry cloth shop rag, to rub the surface as clean as possible. If needed, re-apply the goop and let sit another 1/2 hour. Scrape off and wipe down as before. When you are done with this, you can either wash the surface with soap and water, then dry - or else simply wipe it clean with a fresh shop rag.
Bare metal surfaces should then be wiped with a light coat of machine oil to protect them from rust. Motor oil is okay in a pinch, too.
CAUTION: Remember that oily rags or paper towels can spontaneously combust under the right conditions - so dispose of these safely in a metal container.
Subscribe to:
Posts (Atom)











